Sase Security Framework: 10 Powerful Benefits for 2025 Success
Why the SASE Security Framework is Reshaping Enterprise Security
The sase security framework represents a fundamental shift in how organizations protect their digital assets in today’s cloud-first, remote-work world. Here’s what you need to know:
Quick Definition:
- SASE = Secure Access Service Edge (pronounced “sassy”)
- Framework that combines networking (SD-WAN) + security services in one cloud platform
- Replaces traditional perimeter-based security with identity-driven, zero-trust access
- Delivers consistent policies across all users, devices, and locations
The traditional “castle and moat” security model is dead. With 92% of workloads now hosted on cloud platforms and remote work becoming permanent, the old approach of backhauling all traffic through a central data center creates bottlenecks, poor user experience, and massive security gaps.
SASE solves this by bringing security enforcement to the edge – close to users and applications. Instead of trusting anything inside the network perimeter, SASE verifies every user, device, and application request before granting access. This zero-trust approach combined with cloud-native delivery creates a more secure, scalable, and cost-effective security architecture.
The market is responding fast. Gartner predicts the SASE market will grow at 29% annually, reaching over $25 billion by 2027. Companies that deploy multi-factor authentication as part of their SASE strategy can reduce security incidents by up to 99.9%.
I’m Ryan Carter, founder and CEO of NetSharx Technology Partners, where I help mid-market and enterprise organizations steer digital change through cloud technologies. Over the past two years, I’ve guided hundreds of companies through SASE security framework implementations, helping them reduce network costs by 30% while improving their security posture.
Quick sase security framework definitions:
What Is the SASE Security Framework?
The SASE security framework reshapes how modern organizations protect data by replacing location-based trust with continuous, identity-driven controls delivered from the cloud.
Traditional defenses assumed anything inside the LAN was safe; SASE assumes nothing is trusted until verified—user, device, and application included. Because enforcement points run in global points of presence (PoPs), traffic is inspected near the user, eliminating the latency of backhauling everything to a central data center.
Origin & Definition of the SASE Security Framework
Gartner introduced the term “SASE” (pronounced “sassy”) in 2019 after observing that cloud adoption and remote work had dissolved the classic network perimeter. Their research on cloud workload trends predicted that enterprises would converge networking (SD-WAN) and security services into a single, cloud-delivered solution to regain visibility and control.
The timing wasn’t coincidental. By 2019, organizations were struggling with several converging trends that made traditional security architectures increasingly ineffective. The explosion of SaaS applications meant that critical business data was no longer contained within corporate data centers. Remote work was accelerating even before the pandemic, with distributed teams becoming the norm rather than the exception. Mobile devices were proliferating, and the Internet of Things was adding thousands of new endpoints to corporate networks.
These trends created what security professionals call “perimeter dissolution” – the traditional network boundary simply ceased to exist in any meaningful way. The old model of having a strong firewall at the network edge became like having a fortress wall with thousands of gates, each requiring its own security controls.
Gartner’s research identified that organizations needed a fundamentally different approach – one that could provide consistent security policies regardless of where users, applications, or data resided. This led to the formal definition of SASE as the convergence of network security functions with WAN capabilities to support the dynamic, secure access needs of digital enterprises.
SASE vs. Traditional Network Security Models
With legacy hub-and-spoke designs, traffic from a remote employee in Denver might tunnel through a VPN concentrator in Chicago before reaching a SaaS service in Seattle—adding latency, consuming bandwidth, and forcing IT to scale costly on-premises appliances. SASE removes this detour by inspecting traffic in the nearest PoP, applying policy once, and routing it directly to its destination.
The contrast becomes even more stark when you consider the operational overhead of traditional models. In a typical enterprise with 50 branch offices, IT teams might manage dozens of different security appliances – firewalls, VPN concentrators, web proxies, email security gateways, and more. Each device requires individual configuration, monitoring, and maintenance. Software updates must be deployed to each location, often requiring on-site visits or complex remote management procedures.
Traditional models also struggle with consistency. A security policy configured on the headquarters firewall might be slightly different from the same policy on a branch office device, creating gaps that attackers can exploit. When new threats emerge, updating security controls across dozens of locations can take weeks or months.
SASE eliminates these challenges through centralized, cloud-delivered security services. Policy changes are deployed instantly across all locations. New security capabilities are automatically available to all users without hardware upgrades. The operational burden shifts from managing distributed appliances to managing centralized policies.
The performance benefits are equally compelling. Traditional architectures often force internet-bound traffic to backhaul through corporate data centers, even when users are accessing cloud applications. This “tromboning” effect can double or triple latency for remote users. SASE’s distributed architecture means traffic is processed at the nearest point of presence, typically within 30 milliseconds of the user’s location.
Relationship Between SASE and Security Service Edge (SSE)
Security Service Edge (SSE) is the security-only slice of SASE. Many organizations deploy SSE first—secure web gateway (SWG), cloud access security broker (CASB), firewall as a service (FWaaS), and zero trust network access (ZTNA)—then tackle SD-WAN later.
This phased approach makes sense for several reasons. First, security often presents the most urgent business case. Organizations dealing with increasing cyber threats, compliance requirements, or remote access challenges can realize immediate value from SSE deployment. Second, SSE implementation typically requires less coordination with network operations teams, making it easier to pilot and deploy quickly.
The SSE-first approach also allows organizations to prove the value of cloud-delivered security services before committing to a full network change. Many IT leaders are more comfortable starting with security services while maintaining their existing WAN infrastructure, then adding SD-WAN capabilities once they’ve gained confidence in the cloud platform.
However, organizations that deploy SSE without the networking components of SASE may miss some key benefits. Without SD-WAN’s intelligent path selection and application optimization, users may still experience performance issues when accessing cloud applications. The full value of SASE emerges when networking and security functions work together to optimize both performance and protection.
| Aspect | SASE | SSE |
|---|---|---|
| Scope | Networking + security | Security services only |
| Components | SD-WAN + SWG, CASB, FWaaS, ZTNA, DLP | SWG, CASB, FWaaS, ZTNA, DLP |
| Complexity | Higher | Moderate |
| Best For | Full network modernization | Phased security uplift |
| Implementation Time | 6-12 months | 3-6 months |
| Cost Impact | Higher upfront, greater long-term savings | Lower upfront, moderate savings |
| Performance Benefits | Maximum optimization | Security-focused improvements |
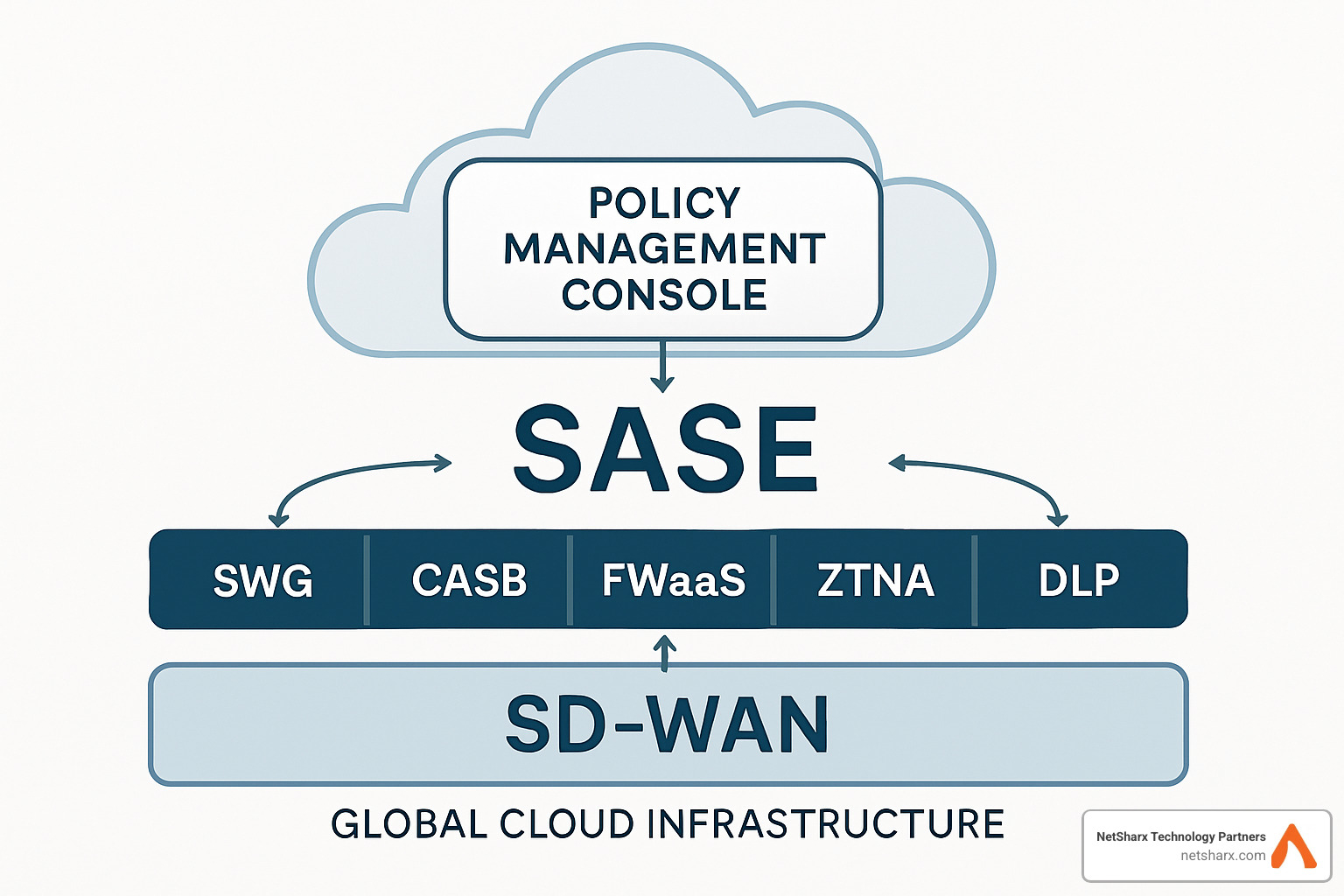
Core Components of a SASE Architecture
The SASE security framework brings together multiple networking and security functions into a unified, cloud-delivered platform. Think of it as the ultimate tech convergence – instead of managing a dozen different security appliances and network devices, everything works together seamlessly from the cloud.
Networking Pillar: SD-WAN Backbone
Software-Defined Wide Area Network (SD-WAN) forms the networking foundation of any SASE implementation. If traditional networking is like having fixed train routes, SD-WAN is like having a smart GPS that automatically finds the best path for your data.
Unlike traditional WAN technologies that rely on expensive MPLS circuits, SD-WAN creates an intelligent overlay network that can use any transport method. The application awareness capability is particularly impressive – SD-WAN can identify and prioritize different types of traffic automatically. Your video conference with an important client gets the premium lane, while that large file backup happens in the background without affecting performance.
Dynamic path selection means the system continuously monitors network conditions and automatically routes traffic over the best-performing path. When the primary internet connection has issues, traffic instantly fails over to backup links.
The intelligence built into modern SD-WAN solutions goes far beyond simple failover. Advanced implementations use machine learning algorithms to predict network congestion and proactively reroute traffic before users experience performance degradation. This predictive capability is particularly valuable for real-time applications like voice and video conferencing, where even brief interruptions can significantly impact user experience.
Traffic steering capabilities allow SD-WAN to make intelligent routing decisions based on application requirements and business policies. Critical applications can be automatically routed over premium connections, while less important traffic uses lower-cost links. This granular control helps organizations optimize both performance and costs.
WAN optimization features built into SD-WAN include data deduplication, compression, and caching. These technologies can reduce bandwidth consumption by 50-90% for certain types of traffic, making it possible to deliver excellent application performance even over lower-bandwidth connections.
In our experience at NetSharx, organizations typically see 30-50% cost savings when migrating from MPLS to SD-WAN as part of their SASE implementation. But the benefits extend beyond cost reduction. The agility that SD-WAN provides – the ability to quickly add new sites, adjust bandwidth, or implement new policies – often proves even more valuable than the direct cost savings.
Security Pillar: The Five Essential Cloud Services
The security components of SASE deliver comprehensive protection without requiring on-premises hardware. These five services work together like a well-coordinated security team, each specializing in different aspects of threat protection while sharing intelligence and coordinating responses.
Secure Web Gateway (SWG) acts as a cloud-based proxy that inspects all web traffic for threats, malware, and policy violations. Modern SWGs can decrypt and inspect SSL/TLS traffic at scale – something that was nearly impossible with traditional appliances.
The evolution of SWG technology has been remarkable. Early web proxies could only inspect unencrypted HTTP traffic, leaving huge blind spots as websites moved to HTTPS. Today’s cloud-delivered SWGs can decrypt and inspect encrypted traffic at massive scale, analyzing not just the content but also the behavior patterns that might indicate threats.
Advanced threat protection capabilities include sandboxing suspicious files in isolated environments, analyzing their behavior, and blocking them if malicious activity is detected. Machine learning algorithms continuously analyze web traffic patterns to identify new threats that haven’t been seen before.
URL filtering and categorization has evolved from simple blacklists to dynamic, AI-powered classification systems that can categorize new websites in real-time. This capability is crucial as attackers increasingly use newly registered domains and frequently change their infrastructure to evade detection.
Cloud Access Security Broker (CASB) provides visibility and control over cloud application usage. CASB can detect shadow IT, enforce data loss prevention policies, and ensure compliance with regulations like GDPR or HIPAA across all cloud services.
The challenge that CASB addresses has grown exponentially with cloud adoption. The average enterprise now uses over 1,000 different cloud applications, many of which are adopted by individual departments without IT oversight. This “shadow IT” creates significant security and compliance risks that traditional security tools can’t address.
API-based CASB solutions integrate directly with cloud applications to provide deep visibility and control. They can monitor user activities, detect unusual behavior patterns, and enforce granular access controls. For example, a CASB might detect that a user is downloading an unusually large number of files from a cloud storage service and automatically restrict their access pending investigation.
Inline CASB capabilities inspect traffic in real-time as users access cloud applications, providing immediate threat detection and policy enforcement. This approach is particularly effective for protecting against data exfiltration and ensuring that sensitive information doesn’t leave the organization through unauthorized channels.
Firewall as a Service (FWaaS) delivers next-generation firewall capabilities from the cloud, including intrusion prevention, application control, and threat intelligence. Unlike traditional firewalls that create choke points, FWaaS scales automatically with demand.
The scalability advantage of FWaaS becomes apparent during traffic spikes or DDoS attacks. Traditional firewalls have fixed processing capacity – when traffic exceeds their limits, they either drop connections or become performance bottlenecks. Cloud-delivered FWaaS can automatically scale processing capacity to handle traffic surges without impacting performance.
Threat intelligence integration allows FWaaS to leverage global threat data from millions of endpoints and network sensors. When a new threat is identified anywhere in the provider’s network, protection is automatically deployed to all customers within minutes. This collective defense approach provides much faster threat response than traditional signature-based systems.
Zero Trust Network Access (ZTNA) replaces traditional VPNs with application-specific access controls. Instead of giving users access to entire network segments, ZTNA verifies user identity and device posture before granting access to specific applications.
The security advantages of ZTNA over traditional VPNs are substantial. VPNs typically provide broad network access – once authenticated, users can access any resource on the corporate network. If a VPN account is compromised, attackers gain extensive access to internal systems. ZTNA eliminates this risk by creating individual, encrypted micro-tunnels for each application.
Device posture assessment is a critical component of ZTNA that goes beyond simple user authentication. Before granting access, the system verifies that the user’s device meets security requirements: Is antivirus software installed and up-to-date? Are security patches current? Is the device encrypted? If any requirements aren’t met, access can be denied or restricted until the device is compliant.
Data Loss Prevention (DLP) monitors and controls sensitive data across all channels – web, email, cloud applications, and file transfers. Cloud-delivered DLP can inspect encrypted traffic and apply consistent policies regardless of user location.
Modern DLP solutions use advanced techniques to identify sensitive data beyond simple pattern matching. Machine learning algorithms can identify sensitive information based on context and content patterns, even when it doesn’t match predefined templates. For example, the system might recognize that a document contains sensitive customer information based on the combination of names, addresses, and account numbers, even if the specific format hasn’t been seen before.
Behavioral analytics add another layer of protection by monitoring how users typically interact with sensitive data and flagging unusual activities. If a user who normally accesses a few customer records suddenly downloads thousands of records, the system can automatically block the activity and alert security teams.
Centralized Policy & Visibility Layer
One of the most significant advantages of the SASE security framework is unified policy management. Instead of configuring security rules across dozens of different appliances and interfaces, administrators can define policies once and have them enforced consistently across all users and locations.
This centralized approach transforms IT operations in ways that go far beyond simple convenience. The single-pane-of-glass management means all networking and security functions are managed through one console, but the real value lies in the consistency and coordination this enables.
Policy orchestration ensures that security rules work together harmoniously across different services. For example, when a user is granted access to a specific application through ZTNA, the firewall automatically creates the necessary rules, the DLP system applies appropriate data protection policies, and the SWG adjusts web filtering rules accordingly. This coordination happens automatically, eliminating the manual configuration errors that often create security gaps.
Real-time analytics provide comprehensive visibility into user behavior, application usage, and security threats across the entire organization. But modern SASE platforms go beyond simple reporting to provide actionable intelligence. Machine learning algorithms analyze patterns across millions of data points to identify trends, predict potential issues, and recommend policy adjustments.
Automated policy enforcement takes the burden off IT teams by implementing security controls based on predefined rules and real-time conditions. Policies can be automatically applied based on user identity, device posture, location, application sensitivity, and even time of day. This automation ensures consistent security enforcement while reducing the workload on IT staff.
The visibility capabilities of modern SASE platforms extend to detailed user experience monitoring. IT teams can see not just whether applications are working, but how well they’re performing for different user groups. This insight enables proactive optimization and helps identify issues before they impact business operations.
Benefits, Use Cases, and Market Outlook
The SASE security framework delivers measurable financial, operational, and security benefits for organizations that accept it.
Primary Benefits of the SASE Security Framework
- Cost savings: Removing on-premises firewalls, VPN concentrators, and MPLS circuits typically cuts network and security spend by 20-40%.
- Simplified operations: A single cloud console replaces multiple management interfaces, shrinking tool sprawl and reducing licensing overhead.
- Better user experience: Decisions happen at the edge, so latency is lower and applications feel snappier for remote and branch users.
- Stronger security: Zero-trust verification at every request shrinks the attack surface and limits lateral movement.
- Elastic scale: New users, sites, or cloud workloads can be onboarded in minutes—without waiting for hardware.
Key Use Cases Powering Adoption
- Hybrid and remote workforce: Replace overloaded VPNs with ZTNA for thousands of mobile employees.
- Branch office connectivity: Use SD-WAN and cloud firewalls to give even a “branch-of-one” enterprise-grade protection without local IT staff.
- Cloud migration: Apply uniform controls to IaaS, SaaS, and on-prem resources during and after a move to Azure, AWS, or GCP.
- IoT and 5G: Automatically identify, segment, and secure new device types as they appear on the network.
Future Outlook & Industry Trends
Gartner forecasts a 29% compound annual growth rate (CAGR) for the SASE market, topping US $25 billion by 2027. Single-vendor consolidation is accelerating as organizations favor easier procurement and management. Meanwhile, regulators in more than 130 countries now enforce data-privacy laws, making the centralized policy model of SASE an attractive compliance accelerator.
Implementing the SASE Security Framework: Steps & Best Practices
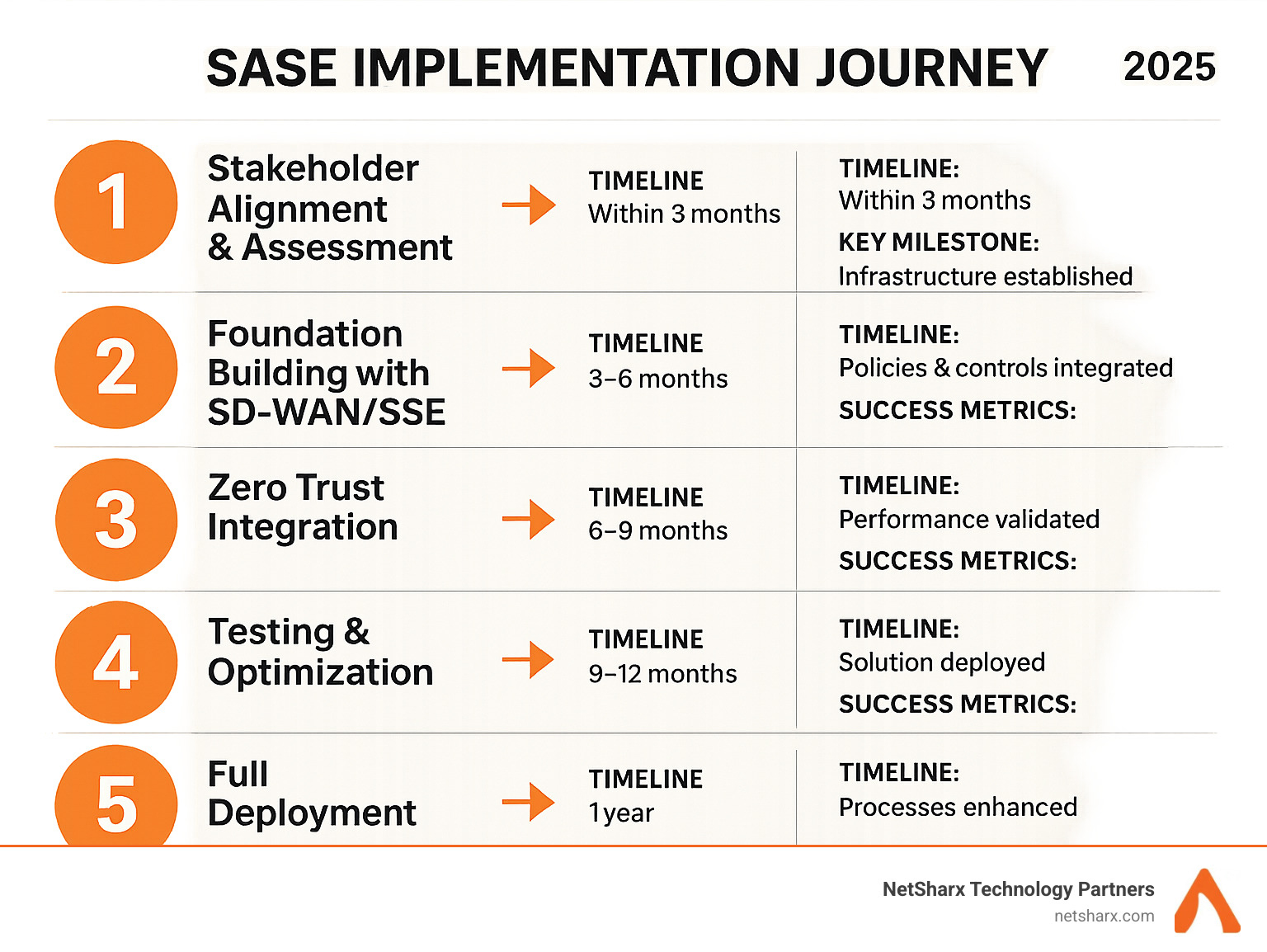
Successful SASE roll-outs follow a phased, business-aligned approach. Below is the condensed 6-step journey we use at NetSharx after guiding hundreds of deployments.
1. Align Stakeholders & Define Objectives
Create a cross-functional team spanning IT, security, compliance, finance, and business leaders. Document current pain points, quantify risks, and set measurable goals such as “reduce branch connectivity spend by 30%” or “enable secure access for 500 remote staff.”
2. Establish the Foundation with SD-WAN or SSE
Choose the path that delivers the fastest win:
- SD-WAN first for high circuit costs or poor application performance.
- SSE first for alert fatigue, remote-access gaps, or urgent compliance needs.
Pilot one or two representative sites to prove value before scaling.
3. Embed Zero Trust & Unified Policies
Integrate identity (e.g., Active Directory, Azure AD, Okta) and enforce least-privilege, application-level access with MFA and device-posture checks. Centralize policy so rules are written once and applied everywhere.
4. Test, Monitor & Optimize
Use digital experience monitoring (DEM) to baseline latency, packet loss, and user satisfaction. Iterate policies, tighten controls, and automate responses based on real-time analytics.
5. Full Deployment & Cut-Over
Expand to additional branches, data centers, and remote users in manageable waves. Decommission legacy VPNs and hardware once traffic levels drop below agreed thresholds.
6. Continuous Improvement
Review metrics quarterly, update policies as threats evolve, and assess emerging SASE features—such as API security or AI-driven anomaly detection—as they mature.
Choosing a Provider
Compare vendors on:
- Integration depth (built vs. acquired services)
- Global PoP density and performance SLAs
- Roadmap alignment with your future requirements
For an objective comparison, explore our secure networking services resources.
Frequently Asked Questions about the SASE Security Framework
What does SASE mean in security?
SASE stands for Secure Access Service Edge, and yes, it’s pronounced “sassy” – which is actually quite fitting for a technology that boldly challenges decades of traditional network security thinking.
In security terms, the SASE security framework represents a complete philosophical shift from the old “castle and moat” approach. Instead of building higher walls around your network perimeter, SASE assumes there is no perimeter at all. Every user, device, and application request gets verified before access is granted, regardless of where the connection comes from.
The SASE security framework combines networking capabilities like SD-WAN with comprehensive security services – firewall, secure web gateway, cloud access security broker, and zero trust network access – all delivered from a single cloud platform. This convergence is what makes SASE so powerful.
What makes this approach is that it’s identity-driven rather than location-driven. Your security policies are tied to who you are and what you’re trying to access, not which network you’re connected to. This means a remote worker in a coffee shop gets the same security protection as someone sitting in the corporate headquarters.
How does the SASE security framework support Zero Trust?
The SASE security framework and zero trust are like peanut butter and jelly – they’re designed to work together perfectly. SASE provides the platform that makes zero trust principles practical and scalable across an entire organization.
Zero trust starts with identity verification. Every time someone tries to access an application, SASE checks their credentials using multi-factor authentication. But it doesn’t stop there – it also verifies that their device meets security requirements. Is the antivirus up to date? Are security patches installed? If not, access gets denied or restricted until the device is compliant.
Micro-segmentation is where SASE really shines. Instead of giving users broad network access, SASE creates individual, encrypted tunnels for each application. Need to check email and access the CRM system? You get two separate, isolated connections. If one gets compromised, the attacker can’t use it to access other systems.
Continuous verification means the security checking never stops. Traditional VPNs verify your identity once when you connect, then trust you for hours. SASE continuously monitors your behavior throughout the session. If you suddenly start accessing unusual files or connecting from a different location, the system can immediately restrict access or require additional verification.
What are the main challenges when adopting SASE?
While SASE offers tremendous benefits, it’s not without its challenges. Understanding these upfront helps organizations plan more effectively and avoid common pitfalls.
The skills gap is probably the biggest hurdle most organizations face. SASE requires expertise in both networking and security domains, which traditionally have been separate specialties. Finding staff who understand SD-WAN optimization AND cloud security policies can be challenging. Many organizations address this by partnering with experienced technology brokers who can provide the necessary expertise during implementation and ongoing management.
Legacy system integration often creates temporary complexity. If you’ve invested heavily in on-premises security appliances, you can’t just rip them out overnight. The transition period requires careful planning to ensure security gaps don’t emerge while you’re migrating systems. This is why we always recommend a phased approach that allows for gradual migration rather than a “big bang” cutover.
Change management affects everyone from IT staff to end users. People who are used to connecting to a VPN and having broad network access may initially resist more restrictive application-specific access controls. The key is communicating the benefits clearly and providing adequate training.
At NetSharx, we help organizations steer these challenges through our agnostic approach to solution engineering. Our extensive provider network means we can recommend the best-fit SASE solution for each organization’s specific requirements, timeline, and budget constraints.
Conclusion
SASE has moved from buzzword to blueprint for securing a cloud-heavy, hybrid-work enterprise. By converging SD-WAN, zero-trust access, and advanced security controls into a single service, organizations can lower costs, boost performance, and reduce risk—all at once.
NetSharx Technology Partners has already guided hundreds of companies through this transition, leveraging our extensive provider network and unbiased solution engineering to deliver measurable results. If you are ready to explore SASE, visit our secure networking services page or contact our Minneapolis team to schedule a no-obligation assessment.
The future of enterprise security is “sassy.” Let’s build it together.