Enterprise identity management is essential for organizations that want to secure access to their sensitive data and networks in today’s digital landscape. By managing digital identities effectively, businesses can ensure that only authorized individuals have access to critical resources, no matter where they work or the devices they use.
Here’s what you need to know about enterprise identity management, in a nutshell:
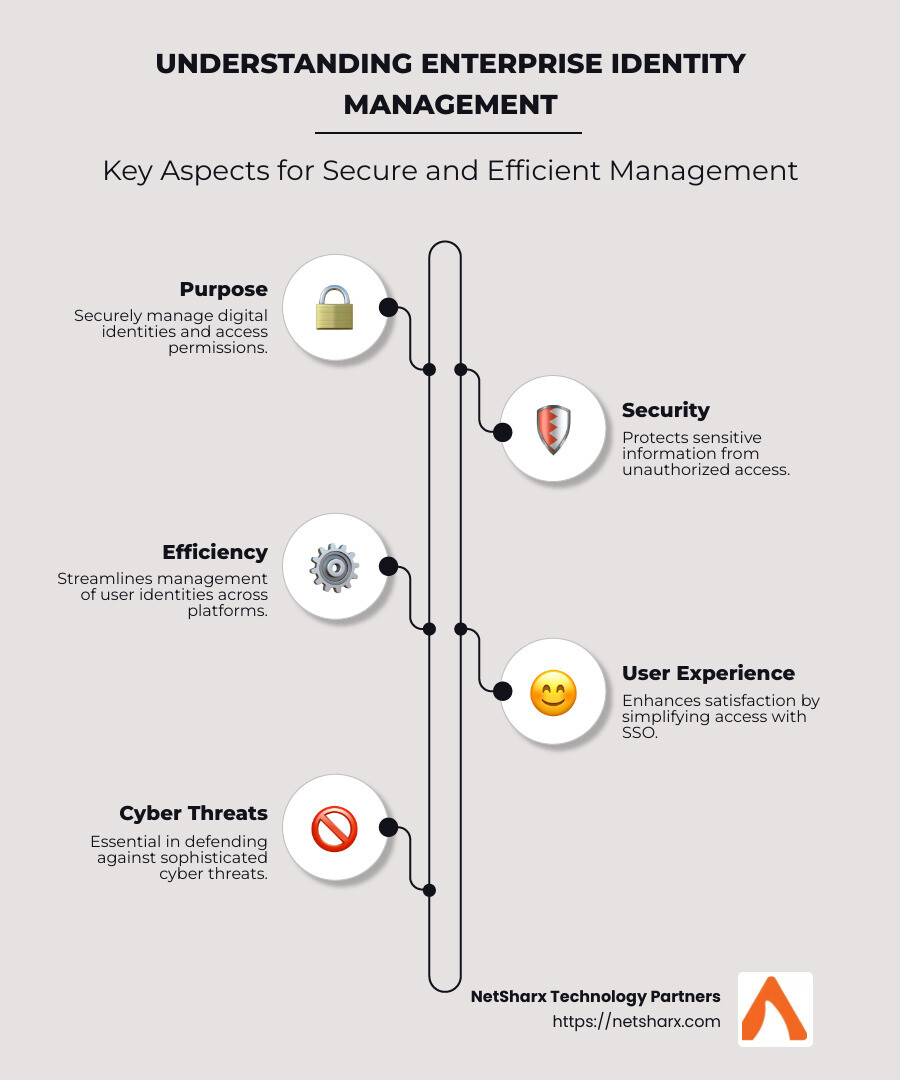
- Purpose: To securely manage digital identities and access permissions.
- Security: Protects sensitive information from unauthorized access.
- Efficiency: Streamlines the management of user identities across platforms.
- User Experience: Improves user satisfaction by simplifying access through Single Sign-On (SSO).
When cyber threats are increasingly sophisticated, having a robust system for managing identities is non-negotiable. This centralized approach not only fortifies security but also improves operational efficiency and boosts user satisfaction.
I’m Ryan Carter, the founder and CEO of NetSharx Technology Partners. With years of experience in guiding enterprises through digital changes, I understand the critical role enterprise identity management plays in securing and streamlining operations, helping organizations steer the complexities of modern technology ecosystems.
Simple guide to enterprise identity management:
– enterprise network protection
– managed firewall services
– penetration testing services
Understanding Enterprise Identity Management
Enterprise identity management is all about managing who gets access to what within an organization. Let’s break it down into three key areas: identity lifecycle, user provisioning, and access control.
Identity Lifecycle
Think of the identity lifecycle as the journey of a digital identity from creation to deletion. It starts when an employee joins the company and ends when they leave. In between, their access needs might change as they move roles or get promoted.
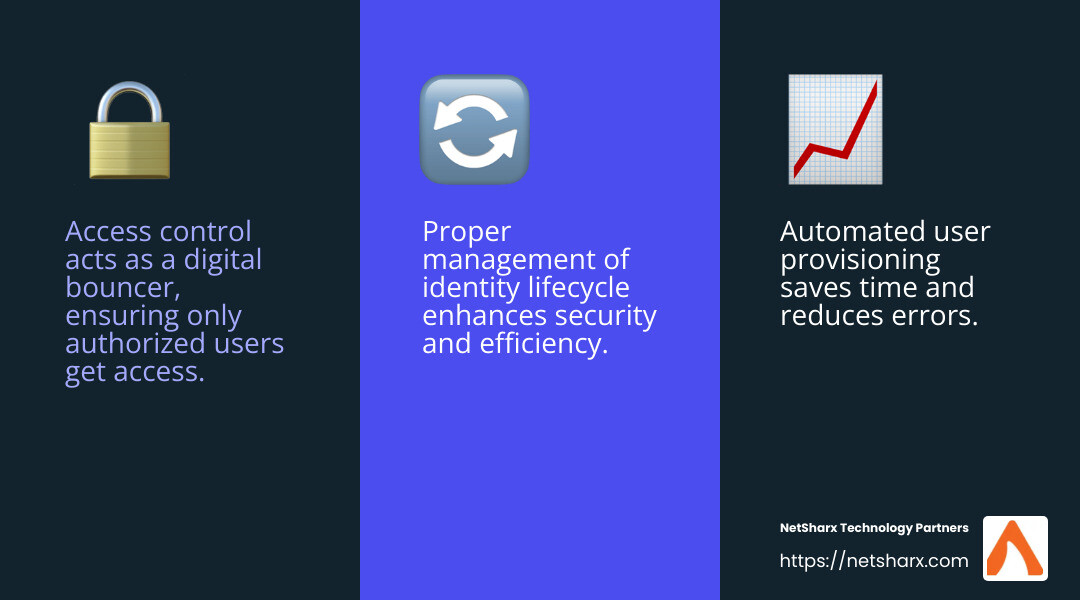
Managing this lifecycle is crucial. It ensures employees have the right access at the right times and prevents former employees from accessing sensitive data. Automated systems can help manage these changes efficiently, reducing the risk of errors.
User Provisioning
User provisioning is the process of setting up a new user’s digital identity. This includes creating their account, setting permissions, and ensuring they have access to the tools they need.
Automated provisioning saves time and reduces mistakes. It helps new employees hit the ground running by giving them immediate access to necessary resources. It also simplifies the process of adjusting access as employees change roles.
Access Control
Access control determines who can access what. It’s like a digital bouncer, ensuring only authorized users get into certain areas. This is vital for protecting sensitive information.
Access control can be fine-tuned using techniques like role-based access control (RBAC), where permissions are assigned based on the user’s role within the organization. This approach helps maintain security while ensuring users have the access they need to perform their jobs.
In summary, understanding and implementing effective enterprise identity management involves managing the entire identity lifecycle, automating user provisioning, and setting strict access controls. This not only improves security but also improves operational efficiency and user satisfaction.
Key Components of Enterprise Identity Management
When it comes to enterprise identity management, three key components stand out: user authentication, authorization, and identity governance. Each plays a vital role in securing access to an organization’s resources.
User Authentication
User authentication is all about verifying who a person is before they access your systems. Think of it as your digital ID check.
Authentication methods can range from simple username and password combinations to more advanced techniques like multi-factor authentication (MFA). MFA requires users to provide two or more verification factors, making it much harder for unauthorized users to gain access.
Single Sign-On (SSO) solutions are also popular. They allow users to log in once and access multiple applications without needing to re-enter credentials. This not only simplifies the user experience but also strengthens security by reducing password fatigue.
Authorization
Once a user is authenticated, the next step is authorization. This decides what a user can access and what actions they can perform.
Imagine a library card—authentication is proving you have a card, while authorization is about what sections of the library you can enter. In digital terms, this might mean access to certain files, applications, or data sets.
Organizations often use role-based access control (RBAC). RBAC assigns permissions based on a user’s role within the company, ensuring they have the access needed to do their job, but nothing more. This minimizes the risk of data breaches by limiting unnecessary access.
Identity Governance
Identity governance is the overarching framework that ensures all identity management processes align with organizational policies and compliance requirements.
This involves regular audits, reporting, and policy enforcement. It’s about making sure that the right people have the right access at the right times, and that any changes in access are tracked and managed appropriately.
Effective identity governance helps prevent unauthorized access and ensures compliance with regulations, which is crucial in today’s data-driven world.
Mastering these key components of enterprise identity management—user authentication, authorization, and identity governance—empowers organizations to improve security, streamline operations, and protect sensitive information from potential threats.
Benefits of Enterprise Identity Management
Implementing enterprise identity management (EIM) offers several key benefits that can significantly improve your organization’s operations.
Security Improvements
Security is a top priority for any organization. With EIM, you can bolster your defenses against unauthorized access and data breaches. By using advanced authentication methods like multi-factor authentication (MFA) and single sign-on (SSO), EIM ensures that only verified users gain access to your systems.
Aite-Novarica’s study with Experian highlights that nearly 64% of consumers are concerned about online security. Implementing EIM can help address these concerns, building trust with your customers and protecting your reputation.
Operational Efficiency
EIM doesn’t just improve security; it also boosts operational efficiency. By automating user provisioning and access controls, you can save time and reduce the risk of human error. No more manually updating user access for hundreds of employees—let the system handle it for you.
For instance, Experian found that poor quality customer contact data negatively impacted 85% of companies’ operations. EIM can help keep your data up-to-date and accurate, ensuring smooth and efficient business processes.
Fraud Prevention
Fraud is a constant threat in the digital world. EIM helps prevent fraud by ensuring that only authorized users can access sensitive information. With a single, persistent identity for each user, you can easily track and monitor access, quickly identifying any suspicious activity.
Experian’s research shows that 67% of consumers are willing to share data if it increases security and prevents fraud. By implementing EIM, you can leverage this willingness to improve your security measures and protect your organization from potential threats.
Incorporating enterprise identity management into your organization not only strengthens security but also improves operational efficiency and helps prevent fraud. These benefits make EIM an essential component for any modern business looking to thrive in an increasingly digital world.
Challenges in Implementing Enterprise Identity Management
Implementing enterprise identity management (EIM) can be a game-changer, but it’s not without its problems. Let’s explore some of the main challenges: integration, scalability, and regulatory compliance.
Integration
A challenge is integration. Many companies have existing systems that are siloed and fragmented. Each department might have its own identity system, making it difficult to create a unified approach. Breaking these silos requires careful planning and collaboration across departments.
A study highlights that successful integration needs clear objectives and buy-in from all stakeholders. Without this, EIM can become another siloed solution rather than a holistic one. Organizations need to be ready to invest time and resources to align different systems and processes.
Scalability
Scalability is another major concern. As companies grow, their EIM systems must be able to handle an increasing number of users and devices. This means ensuring that the system can scale without compromising performance or security.
For example, StrongDM’s Zero Trust PAM platform shows how proper scalability can be achieved by integrating seamlessly with existing tech stacks. This ensures that as your organization grows, your EIM solution can grow with it, maintaining efficiency and security.
Regulatory Compliance
Regulatory compliance is a complex challenge in the field of EIM. With laws like the E.U.’s General Data Protection Regulation and California Consumer Privacy Act, companies must handle personal data with utmost care. Non-compliance can lead to hefty fines and damage to reputation.
Organizations must stay informed about current and upcoming regulations. It’s not just about meeting the minimum requirements; going beyond can be beneficial. A 2023 Experian white paper found that 61% of consumers want full control over their data. By prioritizing compliance, companies can build trust with their customers while avoiding legal pitfalls.
Overcoming these challenges requires a strategic approach and a commitment to ongoing improvement. With the right plan, EIM can become a powerful tool in your organization’s arsenal, providing secure and efficient access to digital resources.
Frequently Asked Questions about Enterprise Identity Management
What is an enterprise identity management system?
An enterprise identity management system is a framework that helps organizations manage digital identities securely. It ensures that only authorized users have access to the company’s resources, such as applications, data, and networks. This system is crucial for maintaining secure access, especially in a world where remote work is common.
Digital identities are created and managed through this system, allowing for streamlined access control and user provisioning. This means employees can have a single identity that grants them access to everything they need, reducing the need for multiple passwords and improving security.
What is the difference between IAM and EIM?
IAM, or Identity and Access Management, is a broad term that encompasses all the processes and technologies used to manage digital identities and control access to resources. EIM, or Enterprise Identity Management, is a specific implementation of IAM within a large organization.
While IAM can be applied to any organization, EIM is custom for enterprises with complex structures and needs. It focuses on integrating identity management across different departments and systems, ensuring a unified approach to access management.
How does enterprise identity management improve security?
Enterprise identity management improves security by ensuring that only authorized users can access sensitive information. It uses advanced methods like single sign-on (SSO) and multi-factor authentication (MFA) to verify identities before granting access.
Access control is another critical aspect. With EIM, organizations can define what resources each user can access, minimizing the risk of unauthorized access. This is vital for protecting against data breaches and fraud.
Moreover, fraud prevention is improved through continuous monitoring and analytics. By tracking user behavior, EIM systems can detect unusual activities that might indicate a security threat, allowing for swift action to prevent potential breaches.
In summary, enterprise identity management not only secures access but also builds a robust defense against cyber threats, making it an essential component of modern organizational security strategies.
Conclusion
At NetSharx Technology Partners, we understand the importance of enterprise identity management in today’s digital landscape. Our approach is simple: provide custom solutions that cater to your specific needs, ensuring a seamless transition and robust security.
Why Choose NetSharx?
We offer technology change without the headaches. Our team of agnostic solution engineers works tirelessly to find the best fit for your organization. With access to over 330 providers, we guarantee competitive pricing and custom solutions. Our unbiased approach means we focus on what works for you, not what benefits us.
Custom Solutions for Every Challenge
Whether you’re dealing with integration issues, scalability concerns, or regulatory compliance, we’ve got you covered. Our comprehensive support ensures that your enterprise identity management system is not just implemented but optimized for your unique environment.
Accept Technology Change
Change can be daunting, but it doesn’t have to be. With NetSharx, you can accept technology change confidently. Our experts will guide you through every step, from planning to execution, ensuring a smooth transition and long-term success.
In the world of cybersecurity, staying ahead is crucial. Let us help you secure your digital future with a robust enterprise identity management system. Explore our cybersecurity solutions today.