It Cyber Security Consultant: 7 Powerful Benefits in 2025
Why Your Business Needs an IT Cyber Security Consultant
An it cyber security consultant is a specialized professional who identifies security vulnerabilities, assesses risks, and implements solutions to protect your organization’s digital assets from cyber threats. With data breach costs averaging $4.88 million globally and cyberattacks increasing by nearly 500% in recent years, these experts have become essential for businesses of all sizes.
Quick Answer: What Does an IT Cyber Security Consultant Do?
- Risk Assessment: Evaluate your current security posture and identify vulnerabilities
- Solution Design: Develop customized security strategies and implement protective measures
- Incident Response: Manage security breaches and minimize damage when attacks occur
- Compliance Support: Ensure your organization meets industry regulations (HIPAA, GDPR, etc.)
- Ongoing Monitoring: Provide continuous threat detection and security management
- Staff Training: Educate employees on security best practices and threat awareness
The cybersecurity consulting market is booming for good reason. The U.S. Bureau of Labor Statistics projects 32% growth in information security analyst roles through 2032 – far above the 8% average for all occupations. This explosive demand reflects a harsh reality: 90% of security threats originate from within organizations, often due to human error or inadequate security measures.
Modern cyber threats evolve at breakneck speed. Ransomware attacks, data breaches, and sophisticated phishing campaigns can cripple operations overnight. For overwhelmed IT departments juggling multiple priorities and tight budgets, partnering with the right cybersecurity consultant isn’t just helpful – it’s often the difference between staying secure and becoming another breach statistic.
What Does an IT Cyber Security Consultant Do?
Think of an it cyber security consultant as your organization’s digital bodyguard – someone who knows exactly where the bad guys might try to break in and how to stop them. These security experts combine deep technical knowledge with business savvy to protect what matters most: your data, your reputation, and your bottom line.
The role goes far beyond just installing firewalls and antivirus software. A skilled cybersecurity consultant starts by conducting comprehensive security assessments that examine every corner of your digital infrastructure. They’re looking for vulnerabilities in your systems, networks, and processes – because sometimes the biggest security hole is a policy that nobody follows.
Penetration testing represents one of their most valuable services. Essentially, they become ethical hackers, trying to break into your systems using the same techniques that real criminals would use. The difference? They’re on your side, and they’ll show you exactly how to fix what they found. These tests often reveal surprising vulnerabilities – from unpatched software to misconfigured databases that expose sensitive customer information.
When things go wrong, an it cyber security consultant leads the charge in incident response. They contain the threat, minimize damage, and preserve evidence for potential legal action. This involves coordinating with multiple stakeholders, from IT teams to legal counsel, while maintaining clear communication with executive leadership about the scope and impact of security incidents.
Compliance support represents another crucial responsibility, helping organizations steer complex regulations like GDPR and HIPAA that can result in millions in fines. Consultants stay current with evolving regulatory requirements across different jurisdictions, ensuring organizations maintain compliance even as regulations change and business operations expand into new markets.
Many consultants also serve as Virtual Chief Information Security Officers (VCISOs), providing executive-level security leadership without the full-time executive salary. Through managed security services and 24/7 monitoring via Security Operations Centers (SOCs), they provide continuous vigilance against evolving threats. This model has become particularly popular among mid-sized organizations that need strategic security guidance but can’t justify the cost of a full-time CISO.
Specialized Service Areas
Modern cybersecurity consultants often specialize in specific domains to provide deeper expertise. Cloud security specialists focus on securing AWS, Azure, and Google Cloud Platform environments, addressing unique challenges like container security, serverless architecture protection, and cloud-native threat detection.
Industrial Control Systems (ICS) security consultants work with manufacturing, energy, and utility companies to protect operational technology environments. These specialists understand the unique requirements of systems that control physical processes and can’t be easily patched or updated.
Privacy consultants specialize in data protection regulations, helping organizations implement privacy-by-design principles and manage complex data governance requirements across multiple jurisdictions.
Key Deliverables from an IT Cyber Security Consultant
Professional cybersecurity consultants provide concrete deliverables that justify their investment. Security roadmaps outline your current security posture, identify gaps, and provide a clear path forward with realistic timelines and budget estimates. These roadmaps typically span 12-36 months and include prioritized recommendations based on risk levels and available resources.
Security architecture documentation serves as the blueprint for protecting your digital infrastructure, specifying required security controls and how different security tools should work together. This documentation becomes invaluable during audits and helps ensure consistent security implementation across the organization.
Incident response playbooks provide step-by-step procedures for handling security emergencies, while awareness training programs address the human element of cybersecurity since human error causes approximately 95% of successful cyber attacks. These training programs are customized to address specific threats relevant to each organization’s industry and risk profile.
Risk assessment reports quantify potential threats and their business impact, helping executives make informed decisions about security investments. These reports translate technical vulnerabilities into business language, showing potential financial losses, regulatory penalties, and reputational damage from various threat scenarios.
Core Services & Engagement Lifecycle
Working with an it cyber security consultant follows a thoughtful, structured approach that builds security improvements step by step. The engagement lifecycle typically unfolds across three distinct phases: assessment, implementation, and ongoing management.
According to IBM’s Cost of a Data Breach Report, organizations with fully deployed security AI and automation experienced breach costs that were $1.76 million lower than those without these capabilities. That’s the kind of measurable impact a well-executed consulting engagement can deliver.
Phase 1 – Assess
Every successful security change starts with understanding exactly where you stand today. Asset inventory forms the foundation, cataloging every system, application, database, and network connection in your environment. This process often surprises organizations – I’ve seen companies find forgotten servers running critical applications and unused cloud instances that had been running for years.
Gap analysis compares your current security controls against established frameworks like NIST or ISO 27001. Risk quantification translates technical vulnerabilities into language executives understand: dollars and cents, calculating potential financial losses from various threat scenarios.
Phase 2 – Implement
Implementation focuses on deploying security controls that will actually protect your organization. Firewall configuration and network segmentation create the first line of defense. Identity and Access Management (IAM) systems ensure only the right people can access sensitive resources, including single sign-on solutions and multi-factor authentication.
Zero Trust architecture assumes every user and device could be compromised, verifying every access request regardless of location. Encryption deployment protects data whether it’s stored in databases or traveling across networks.
Phase 3 – Manage & Evolve
Managed Detection and Response (MDR) services provide 24/7 monitoring and incident response capabilities. SIEM tuning optimizes monitoring systems to reduce false positives while ensuring genuine threats get detected quickly. Tabletop exercises test incident response procedures, while metrics dashboards provide ongoing visibility into security program effectiveness.
Skills, Certifications & Career Path
The most successful it cyber security consultant professionals master a blend of technical expertise, business savvy, and communication skills. The cybersecurity consulting field rewards this unique combination handsomely, with information security analysts earning an average of $107,332 annually, while experienced consultants often command $150,000 or higher. Senior consultants with specialized expertise in areas like cloud security or compliance can earn $200,000 or more annually.
The U.S. Bureau of Labor Statistics projects 32% growth in information security roles through 2032 – four times faster than the average for all occupations. In an era where artificial intelligence threatens many traditional jobs, cybersecurity consulting remains refreshingly human-centric, requiring critical thinking, creative problem-solving, and relationship-building skills that technology cannot easily replicate.
Must-Have Technical Competencies
Network protocols knowledge forms the bedrock of consulting credibility. A solid it cyber security consultant needs deep familiarity with TCP/IP, DNS, DHCP, and routing protocols. Understanding how data flows through networks enables consultants to identify potential interception points and design appropriate security controls.
Scripting capabilities in Python, PowerShell, and Bash separate efficient consultants from those still clicking through interfaces manually. Automation skills become increasingly important as organizations seek to scale security operations without proportionally increasing staff. Python expertise is particularly valuable for security automation, threat hunting, and custom tool development.
Cloud platform expertise has transformed from “nice to have” to “absolutely essential” as organizations migrate workloads to AWS, Azure, and Google Cloud Platform. Consultants must understand cloud-native security services, identity and access management in cloud environments, and how to secure hybrid architectures that span on-premises and cloud infrastructure.
Security tool proficiency spans vulnerability scanners like Nessus and Qualys, penetration testing frameworks including Metasploit and Burp Suite, SIEM platforms such as Splunk and QRadar, and endpoint detection solutions like CrowdStrike and SentinelOne. Hands-on experience with these tools enables consultants to make informed recommendations and assist with implementation.
Forensics and incident response skills become critical when security incidents occur. Consultants need familiarity with forensic tools like EnCase and FTK, memory analysis techniques, and evidence preservation procedures that maintain legal admissibility.
Industry-Recognized Certifications
CISSP (Certified Information Systems Security Professional) remains the gold standard for security leadership roles, demonstrating broad knowledge across eight security domains. The certification requires five years of relevant experience and ongoing continuing education.
CISM (Certified Information Security Manager) focuses on management and governance aspects of information security, making it particularly valuable for consultants who work with executive teams and board members.
CISSP (Certified Ethical Hacker) and OSCP (Offensive Security Certified Professional) validate penetration testing skills, while GCIH (GIAC Certified Incident Handler) demonstrates incident response expertise.
Cloud-specific certifications like AWS Certified Security – Specialty and Microsoft Azure Security Engineer Associate have become increasingly important as organizations migrate to cloud platforms.
Essential Soft Skills
Communication skills often matter more than technical expertise when determining consulting success. The ability to translate complex security jargon into business language determines whether recommendations get implemented with executive backing. Successful consultants can explain why a particular vulnerability matters to someone who doesn’t understand the technical details.
Project management capabilities ensure consulting engagements deliver promised outcomes within agreed timelines and budgets. Many consultants pursue PMP (Project Management Professional) certification to formalize these skills.
Business acumen helps consultants understand how security decisions impact organizations, while client relationship management transforms one-time engagements into long-term partnerships. The most successful consultants become trusted advisors who understand their clients’ business objectives and industry challenges.
Presentation skills are crucial for delivering findings to executive audiences and board members. Consultants must be comfortable presenting to groups ranging from technical teams to C-suite executives, adapting their communication style and content to each audience.
Career Progression and Specialization Paths
The cybersecurity consulting journey typically begins with analyst roles focused on specific technical domains like vulnerability assessment or security monitoring. These positions provide foundational experience and exposure to various security tools and methodologies.
Security engineer positions involve solution design and implementation, requiring deeper technical skills and the ability to architect comprehensive security solutions. Engineers often specialize in particular technologies or industry verticals.
It cyber security consultant positions require the full range of technical and business skills, combining hands-on technical work with client relationship management and business development responsibilities. Consultants typically manage multiple client relationships simultaneously and may lead small project teams.
Senior consultant roles involve managing larger, more complex engagements and mentoring junior staff. Senior consultants often develop specialized expertise in high-demand areas like cloud security, compliance frameworks, or incident response.
Virtual Chief Information Security Officer (VCISO) roles represent the consulting career pinnacle, providing executive-level security leadership to organizations. VCISOs combine deep technical knowledge with strategic business thinking and executive communication skills.
Building Your Consulting Practice
Many successful consultants eventually establish independent practices or join boutique consulting firms. Business development skills become crucial for independent consultants who must generate their own client relationships. Thought leadership through speaking engagements, published articles, and industry participation helps establish credibility and attract clients.
Professional networking within industry organizations like ISACA, (ISC)², and local security groups provides opportunities to meet potential clients and stay current with industry trends. Many consulting opportunities arise through professional referrals rather than formal procurement processes.
Trends, Challenges & Future Outlook
The cybersecurity landscape is changing rapidly. Artificial intelligence has become a double-edged sword, helping detect threats faster while enabling a nearly 500% increase in email-based attacks during 2023. Attackers now use AI to craft phishing emails so convincing that even security-aware employees fall for them.
Quantum computing represents a future threat that smart organizations are already planning for through post-quantum cryptography. Supply chain attacks like SolarWinds have shown how one compromised vendor can impact thousands of organizations simultaneously.
Internet of Things (IoT) devices are everywhere now, each representing a potential entry point for attackers. Remote work has permanently changed the security landscape, accelerating adoption of zero-trust architectures and cloud-based security services.
Emerging Service Models
Governance, Risk, and Compliance as a Service (GRCaaS) has become popular among smaller organizations that need compliance expertise without full-time staff. Extended Detection and Response (XDR) platforms integrate multiple security tools into single platforms, requiring specialized implementation expertise.
The fractional CISO model provides strategic security guidance on a part-time basis, giving smaller companies access to senior expertise while allowing experienced consultants to diversify their client base.
Regulatory Momentum
The Digital Operational Resilience Act (DORA) creates comprehensive cybersecurity requirements for financial services organizations. Healthcare organizations continue struggling with HIPAA compliance while adopting innovative technologies. The Cybersecurity Maturity Model Certification (CMMC) program affects any organization working with the U.S. Department of Defense, while SEC cybersecurity disclosure rules require public companies to report material incidents within four business days.
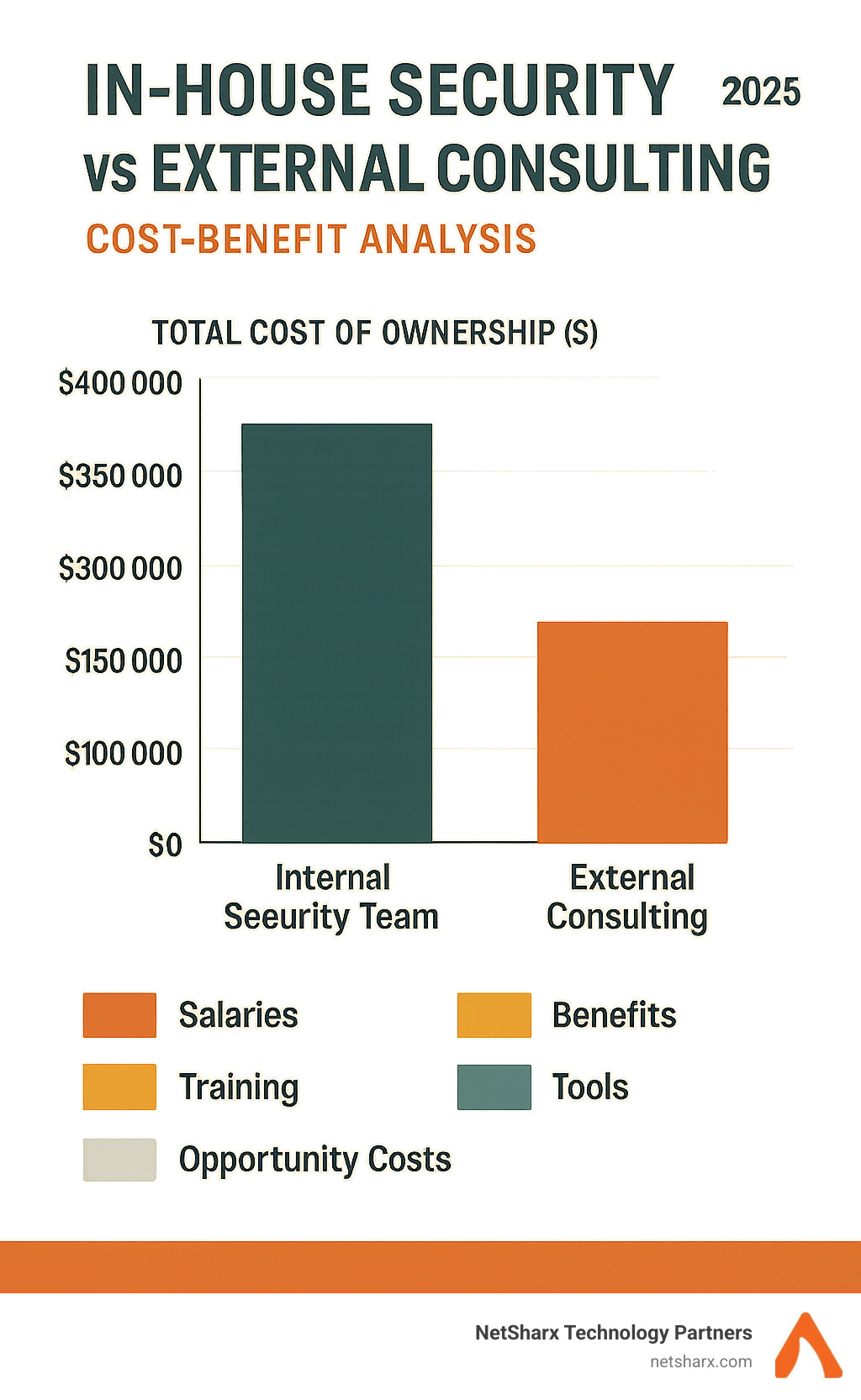
In-House Security vs External Consulting: Cost-Benefit Analysis
Organizations face complex decisions when structuring their cybersecurity capabilities. Building internal security teams provides dedicated resources but requires significant investment in hiring, training, and retaining specialized talent. A single senior security engineer’s salary and benefits can exceed $150,000 annually, not including security tools and training costs.
External consulting offers access to specialized expertise and industry best practices without long-term employment commitments. Consultants bring experience from multiple client engagements and stay current with emerging threats through continuous professional development.
When to Augment Rather Than Hire
Mergers and acquisitions create immediate security assessment requirements that exceed internal team capacity. Compliance deadlines often create urgent requirements for specialized knowledge. Breach aftermath situations require immediate access to incident response expertise and digital forensics capabilities.
Major technology initiatives like cloud migrations or security tool implementations benefit from consulting expertise during planning and execution phases, with internal teams handling ongoing management after completion.
Selecting the Right Partner
Experience evaluation should focus on relevant industry knowledge and technical expertise. Look for consultants who have worked with organizations similar to yours in size, industry, and regulatory environment. Certification verification ensures consultants possess validated expertise, while engagement model flexibility allows relationships to evolve as needs change.
Cultural fit assessment ensures productive, collaborative relationships. During initial discussions, evaluate whether consultants understand your organizational culture and decision-making processes.
Frequently Asked Questions about Cybersecurity Consulting
What Industries Hire Consultants Most?
Financial services leads cybersecurity consulting demand due to strict regulations and constant attack threats. Healthcare organizations increasingly depend on consultants as they adopt digital change while maintaining HIPAA compliance. Government agencies represent another major market, especially with CMMC program requirements.
Small and medium-sized businesses are becoming the fastest-growing consulting segment, facing the same cyber threats as Fortune 500 companies but rarely having dedicated security teams.
How Do Consultants Manage Incident Response?
When cyber incidents strike, consultants manage response through detailed incident response playbooks developed specifically for each organization. Digital forensics capabilities allow consultants to preserve evidence while determining how attackers gained access.
Recovery coordination involves more than getting systems online – consultants work with internal teams and vendors to restore normal operations while implementing additional safeguards. Communication management helps organizations steer complex notification requirements for regulatory agencies, law enforcement, and customers.
What Is the Average Salary and Demand Outlook?
Information security analysts earn a median annual salary of $120,360, with experienced consultants often earning significantly more. The Bureau of Labor Statistics projects 32% growth through 2032 – four times higher than average occupations.
Geographic location affects salaries significantly, with consultants in major metropolitan areas earning 20-30% more than the national average. Specialization premiums reward consultants with expertise in high-demand areas like cloud security and compliance frameworks.
Conclusion
The cybersecurity consulting field is experiencing explosive growth, with 32% projected expansion through 2032. As cyber threats become more sophisticated and regulations tighten across industries, skilled it cyber security consultants have never been more critical. With average data breach costs reaching $4.88 million, organizations can’t afford to operate without professional security expertise.
Successful consultants combine technical expertise with business acumen, translating complex security concepts into actionable business strategies. The consulting lifecycle – from assessment through implementation and ongoing management – reflects how mature this field has become, moving far beyond simple antivirus installation to comprehensive security program architecture.
The choice between internal security teams and external consulting often favors consulting for many organizations, especially smaller ones. When a single senior security engineer costs $150,000+ annually, consulting frequently delivers better value and broader expertise access.
Whether you’re considering a cybersecurity consulting career or your organization needs security expertise, the key insight is that relationships matter more than technology. The most successful engagements create lasting partnerships where consultants become trusted advisors who understand business objectives while strengthening security posture.
At NetSharx Technology Partners, our agnostic approach and extensive provider network enable us to connect you with cybersecurity consultants who match your specific requirements and organizational culture. We’ve helped clients reduce security costs by 30% while dramatically improving their security posture through the right consulting partnerships.
Your digital future depends on making smart security decisions today. The expertise exists to keep you secure – the question isn’t whether you can afford professional cybersecurity consulting, but whether you can afford to operate without it.
Learn more about our cybersecurity solutions and find how the right consulting partnership can safeguard your organization while supporting your growth objectives.