Enterprise mobile security solution is a vital shield for any business navigating today’s digital landscape. Mobile devices have become integral to modern enterprise functioning, driving communication and productivity. However, their widespread use also presents significant security challenges. To address these, organizations need a robust enterprise mobile security solution that safeguards both the devices and the data they handle, ensuring seamless productivity.
Here’s why it matters:
- Mobile devices are central to business operations, offering best convenience but also vulnerability.
- An effective security solution protects against threats without hindering the productivity these devices offer.
- Key components should include managing devices, defending against threats, and safeguarding identity and access.
As a founder and CEO of NetSharx Technology Partners, I focus on helping organizations leverage the right technologies, including enterprise mobile security solution, to fortify their operations against threats.
Enterprise mobile security solution helpful reading:
– enterprise mobile application management
– enterprise mobile applications
– enterprise mobile computing
Why Enterprise Mobile Security is Critical
In today’s business world, remote work is no longer a trend—it’s the norm. According to a 2023 Pew Research study, 41% of employees with jobs that can be done remotely work on a hybrid basis. This means they often use personal devices for work tasks. While this flexibility boosts productivity, it also raises significant security concerns.
Data protection is one of the primary reasons why an enterprise mobile security solution is essential. Mobile devices store and access sensitive business information. If a device is compromised, it can lead to data breaches that expose confidential data. This is a risk no organization can afford to ignore.
Cyberattacks targeting mobile devices are on the rise. The Lookout Remote Work Report found that 92% of remote workers use their personal tablets or smartphones for work tasks. Yet, many existing security solutions fall short, leaving gaps in protection. Common threats include:
- Phishing attacks: These trick users into revealing sensitive information.
- Malicious apps: Some apps can steal data or damage devices.
- Unsecured networks: Public Wi-Fi can be a gateway for hackers.
Organizations must implement robust security measures to combat these threats. This includes mobile device management (MDM) and mobile threat defense (MTD) to monitor and protect devices from potential threats.
NetSharx Technology Partners in Minneapolis, MN, focuses on providing comprehensive enterprise mobile security solutions. These solutions not only protect data but also ensure that employees can work securely from any location.
In summary, as remote work continues to grow, so does the need for effective mobile security. Protecting mobile devices is crucial to safeguarding sensitive business data and maintaining productivity.
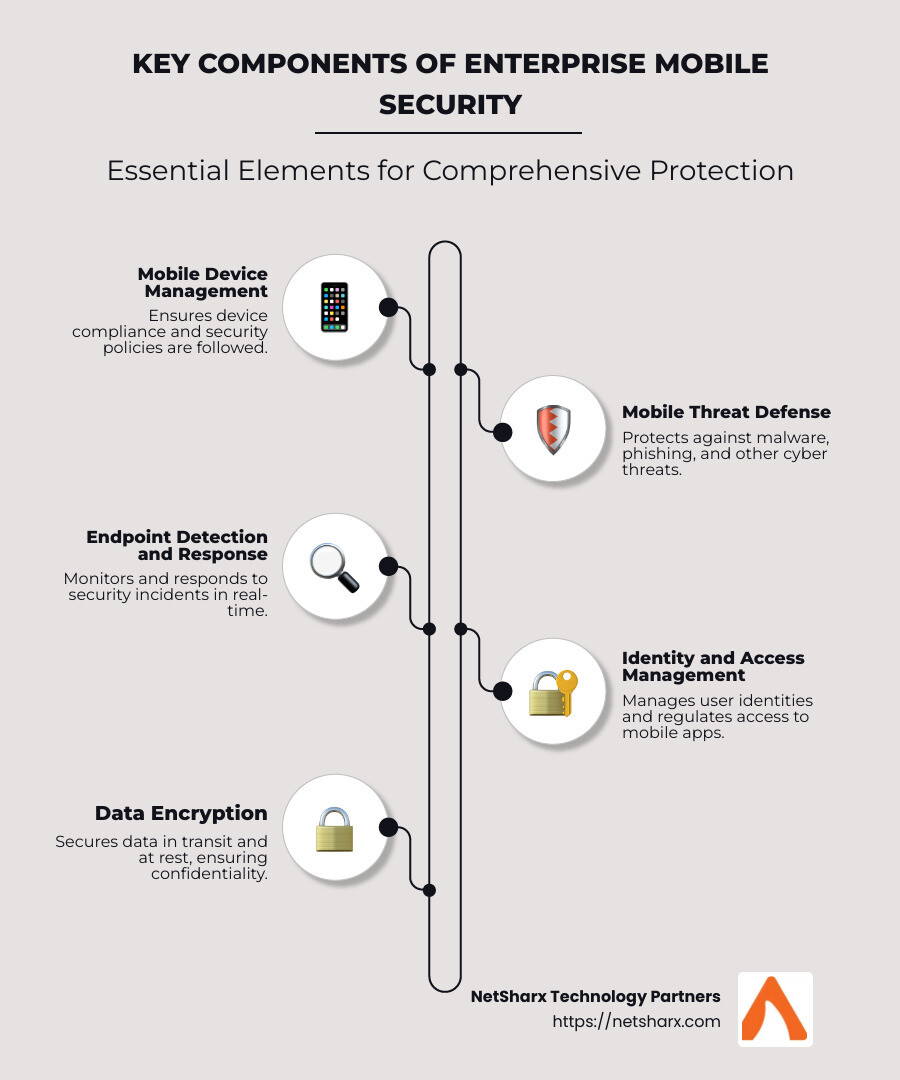
Key Components of an Enterprise Mobile Security Solution
When it comes to protecting mobile devices in the business world, understanding the key components of an enterprise mobile security solution is essential. Let’s explore the main elements that make up an effective strategy.
Mobile Device Management (MDM)
Mobile Device Management (MDM) is like having a security guard for every device in your company. It helps manage and enforce security policies on organization-owned devices. With MDM, you can track devices, enforce encryption, manage applications, and perform remote wipes if a device is lost or stolen. This ensures your devices meet security standards before they access company resources.
For example, if an employee’s phone is lost, MDM allows IT to remotely wipe sensitive data to prevent unauthorized access. This is crucial for maintaining data security in today’s mobile-centric work environment.
Mobile Threat Defense (MTD)
Mobile Threat Defense (MTD) acts as a shield against various threats targeting mobile devices. This component focuses on detecting and preventing threats like malware, phishing attacks, and network intrusions.
With MTD, organizations can monitor mobile devices for suspicious activities and respond quickly to potential threats. This proactive approach is essential as cyberattacks become more sophisticated.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a vital tool for monitoring and protecting mobile endpoints. EDR solutions continuously track device activities to detect anomalies and potential threats.
By using threat intelligence and behavioral analysis, EDR can identify threats early and automate responses to mitigate damage. This ensures that any suspicious activity is quickly addressed, reducing the risk of data breaches.
Identity and Access Management (IAM)
Identity and Access Management (IAM) ensures that only authorized users can access company data and applications. IAM systems use technologies like multi-factor authentication and single sign-on to verify user identities.
These systems control how, when, and where employees can access corporate resources, adding an extra layer of security. By implementing IAM, companies can reduce the risk of unauthorized access and safeguard sensitive information.
Incorporating these components into your enterprise mobile security strategy is crucial for protecting your organization from mobile threats. Each element plays a unique role in ensuring that mobile devices are secure and that sensitive data remains protected.
By leveraging these tools, businesses can build a robust defense against the changing landscape of mobile threats.
Best Practices for Implementing Enterprise Mobile Security
Implementing an effective enterprise mobile security solution involves more than just technology. It requires well-thought-out strategies and practices to ensure comprehensive protection. Here are some best practices to consider:
Develop a Comprehensive Security Policy
Start with a clear and comprehensive security policy. This policy should outline acceptable use, prohibited activities, and consequences for violations. It should cover both organization-owned and personal devices, ensuring consistency across the board.
Include details on device configuration, application management, and compliance requirements. Specify password standards, encryption protocols, and access controls. This policy acts as the backbone of your mobile security strategy.
Implement Strong Access Controls
Access controls are vital for protecting sensitive data. Use a zero-trust model, which continuously verifies users’ identities and access privileges. This model ensures that employees only access what they need for their roles.
Incorporate multi-factor authentication (MFA) to add an extra layer of security. This means requiring two or more verification steps before granting access, making it harder for unauthorized users to breach your systems.
Conduct Regular Employee Training
Even the best technology can’t compensate for human error. Regular employee training is essential to keep everyone informed about security practices. Teach employees to recognize phishing attempts, handle sensitive data responsibly, and avoid risky behaviors like connecting to unsecured WiFi networks.
Consider conducting phishing simulations and other tests to reinforce training and improve vigilance. An informed workforce is your first line of defense against cyber threats.
Perform Regular Audits and Monitoring
Regular audits help assess the effectiveness of your security measures. They identify potential weaknesses and ensure compliance with your security policy. Use real-time monitoring tools to detect and respond to security incidents promptly.
By continuously evaluating your security posture, you can adapt to new threats and maintain robust protection. Regular audits also demonstrate your commitment to security, which can be crucial for regulatory compliance and customer trust.
By following these best practices, organizations can improve their enterprise mobile security solution and protect against mobile threats. From developing a robust security policy to conducting regular audits, each step plays a crucial role in safeguarding your business.
Challenges in Enterprise Mobile Security
Navigating enterprise mobile security solutions comes with its own set of challenges. Let’s explore some of the most pressing issues: BYOD policies, the privacy versus security dilemma, and the diverse device ecosystems.
BYOD Policies: Balancing Convenience and Security
Bring Your Own Device (BYOD) policies are becoming increasingly popular. They offer employees the flexibility to use personal devices for work, which can boost productivity and satisfaction. However, they also introduce significant security risks.
The challenge lies in implementing security measures on personal devices without infringing on user privacy or convenience. Companies must strike a balance between protecting corporate data and respecting employee privacy. This often involves creating clear policies that outline security requirements and acceptable use, while also offering support for device security features like encryption and remote wipe capabilities.
Privacy vs. Security: Finding the Right Balance
When it comes to enterprise mobile security, there’s a constant tug-of-war between maintaining security and respecting privacy. Employees are often wary of security measures that might infringe on their personal privacy.
Organizations must engage in open discussions to find a middle ground. It’s essential to communicate the importance of security measures and how they protect not just the company, but the employees’ personal information as well. By being transparent and involving employees in the decision-making process, companies can foster trust and cooperation.
Diverse Device Ecosystems: Managing Complexity
Employees use a wide array of devices with different operating systems and manufacturers. This diversity can complicate security management, as each platform has its unique security features and vulnerabilities.
To tackle this challenge, organizations need a consistent security approach that spans across all devices. Implementing a robust Enterprise Mobility Management (EMM) or Mobile Device Management (MDM) solution can help standardize security protocols and ensure compliance across various device types. These solutions can provide tools for device tracking, compliance checks, and remote management, making it easier to maintain a secure environment.
Addressing these challenges is crucial for building a resilient enterprise mobile security solution. By carefully managing BYOD policies, balancing privacy and security, and handling diverse device ecosystems, organizations can protect their valuable assets and maintain a secure mobile environment.
Frequently Asked Questions about Enterprise Mobile Security Solutions
What is an enterprise mobile security solution?
An enterprise mobile security solution is a comprehensive approach to securing mobile devices used within a business environment. It involves policies, technologies, and practices designed to protect sensitive data and ensure safe access to corporate resources. Key components include threat protection, data encryption, and access management. These solutions aim to prevent unauthorized access and safeguard against threats such as malware and data breaches.
How does mobile device management contribute to security?
Mobile Device Management (MDM) plays a crucial role in enhancing security. It helps organizations track devices, enforce security policies, and ensure compliance with regulations. Device tracking allows IT teams to monitor device locations and usage patterns, while remote wipes enable the secure deletion of data from lost or stolen devices. MDM also performs compliance checks to ensure that devices adhere to company security standards, reducing the risk of data leaks and unauthorized access.
What are the biggest threats to mobile devices in an enterprise?
Mobile devices in enterprises face several significant threats:
- Device theft: Physical loss or theft of devices can lead to unauthorized access to sensitive data.
- Phishing attacks: Cybercriminals often target mobile users with deceptive messages to steal credentials or install malware.
- Unsecured networks: Connecting to public WiFi or other insecure networks can expose devices to interception and attacks.
Organizations must implement robust security measures, such as data encryption and threat protection, to mitigate these risks and protect their mobile assets.
Conclusion
In today’s digital landscape, ensuring the security of mobile devices is no longer optional—it’s a necessity. At NetSharx Technology Partners, we understand the critical role that enterprise mobile security solutions play in protecting your business. As a technology broker, we offer custom solutions custom to meet the unique needs of your organization.
Our approach is simple: we listen to your challenges, understand your goals, and then leverage our extensive provider network to deliver the best-fit solutions. Whether it’s implementing robust mobile device management or enhancing threat protection, our team is here to guide you through every step of your technology change.
Why choose NetSharx?
- Unbiased Solutions: We provide agnostic solution engineering, ensuring that you receive the most effective and cost-efficient options.
- Comprehensive Support: Our team offers end-to-end support, from initial consultation to ongoing management.
- Competitive Pricing: We work to secure the best rates, making advanced security solutions accessible for businesses of all sizes.
As mobile devices continue to reshape the enterprise landscape, it’s crucial to stay ahead of potential threats. Our commitment is to empower you with the tools and strategies needed to secure your mobile ecosystem effectively.
Ready to transform your mobile security strategy? Explore our solutions and drive change with NetSharx Technology Partners.
By partnering with us, you ensure that your enterprise is not just keeping up with technology change but leading the charge with confidence and security.