Cloud security solutions are essential for safeguarding sensitive data and ensuring the integrity of cloud environments. These solutions focus on:
- Data protection to prevent unauthorized access.
- Threat prevention to identify and neutralize potential cyber threats.
- Compliance management to ensure adherence to applicable regulations.
As organizations transition to cloud platforms, the ability to secure these environments becomes increasingly crucial. Effective cloud security solutions not only protect against data breaches but also improve operational efficiency by integrating with existing IT infrastructures.
I’m Ryan Carter, founder and CEO of NetSharx Technology Partners. With years of experience helping businesses steer the complexities of cloud security solutions, I am committed to guiding organizations through their digital change securely and efficiently. Let’s explore how robust cloud security can shield your business from evolving cyber threats.
Understanding Cloud Security Solutions
Cloud security solutions are the backbone of protecting sensitive information and maintaining the integrity of cloud environments. Let’s break down what makes these solutions so vital.
Cloud Architectures
Cloud architectures are like the blueprint of your digital house. They determine how data flows and is stored. A strong architecture ensures that data moves securely within the cloud. Think of it like building a fortress where every entrance is guarded. Organizations need to ensure their cloud architecture is designed with security in mind, using tools that detect and fix vulnerabilities before they can be exploited.
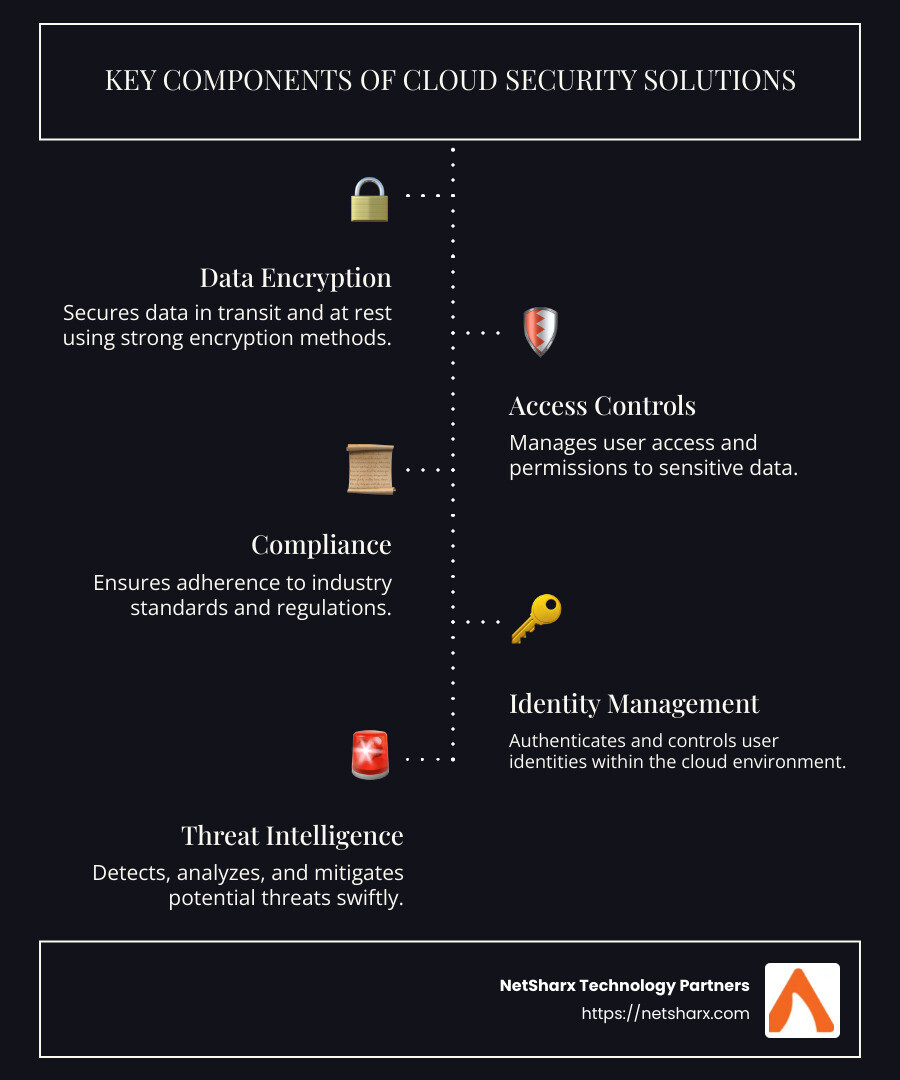
Identity Management
Identity management is about knowing who is accessing your cloud environment and what they are allowed to do. Imagine a digital ID card that verifies a person’s identity before they enter a secure area. This is crucial because, as the research highlights, cloud providers offer thousands of entitlements, which can be tricky to manage without the right tools. Effective identity management prevents unauthorized access and helps maintain control over who can view or modify sensitive data.
Threat Intelligence
Threat intelligence acts like a security camera, constantly monitoring for suspicious activity. It provides insights into potential threats and helps organizations stay one step ahead of cybercriminals. The research emphasizes the importance of having the latest threat intelligence to identify and defend against emerging cyberthreats. By leveraging threat intelligence, businesses can quickly detect and respond to threats, minimizing the risk of data breaches and ensuring a secure cloud environment.
Cloud security solutions are not just about protecting data; they’re about creating a resilient and efficient digital ecosystem. By understanding and implementing robust cloud architectures, effective identity management, and up-to-date threat intelligence, organizations can shield themselves from the constantly evolving cyber landscape.
Next, we’ll dive into the key components of cloud security solutions, focusing on data encryption, access controls, and compliance.
Key Components of Cloud Security Solutions
In the field of cloud security solutions, three critical components stand out: data encryption, access controls, and compliance. Each plays a vital role in safeguarding data and ensuring a secure cloud environment.
Data Encryption
Think of data encryption as a secret code that only authorized users can decipher. It’s like having a lock on your diary that only you can open. In the cloud, encryption protects data both at rest and in transit. This means that even if cybercriminals intercept your data, they can’t read or use it without the encryption key.
A common method is AES-256 encryption, which is known for its robustness and is virtually impossible to break. This level of encryption ensures that sensitive information, like financial data or personal records, remains confidential. By applying consistent encryption across all data, businesses can strike a balance between security and usability, making sure information is both protected and accessible to those who need it.
Access Controls
Access controls are like the bouncers at a club, deciding who gets in and who stays out. They help prevent unauthorized access to sensitive cloud resources. Strong access controls involve verifying identities before granting access and ensuring users have only the permissions they need to do their jobs.
Multi-factor authentication (MFA) is a key part of this strategy. It requires users to provide two or more verification factors to gain access, making it much harder for attackers to use stolen credentials. Effective access controls are crucial for protecting sensitive data and maintaining the integrity of cloud environments.
Compliance
Compliance is all about following the rules and regulations that govern data protection. It’s like having a checklist to ensure you’re doing everything by the book. Regulations such as GDPR and PCI DSS set standards for how data should be handled and protected.
Cloud security solutions assist organizations in aligning with these regulatory frameworks by providing tools that help manage and demonstrate compliance. This includes features like data loss prevention, audit logging, and real-time monitoring. By maintaining compliance, businesses not only avoid hefty fines but also build trust with their customers by proving they take data protection seriously.
These components—data encryption, access controls, and compliance—form the foundation of a robust cloud security strategy. They work together to create a secure environment where data is protected from unauthorized access and breaches.
Next, we’ll explore the top cloud security solutions for 2024, highlighting technologies like Zero Trust Network Access and Cloud Access Security Brokers.
Top Cloud Security Solutions for 2024
As we look ahead to 2024, several cloud security solutions are standing out as essential tools for protecting cloud environments. These solutions are designed to address the unique challenges of cloud security and ensure data protection, threat prevention, and compliance.
Zero Trust Network Access (ZTNA)
Imagine a world where no one is trusted by default, not even once they’re inside the network. That’s the essence of Zero Trust Network Access. ZTNA is like a security guard who checks everyone’s credentials every time they enter a room. It ensures that access to data and applications is granted based on strict verification of identity, device, and context.
ZTNA minimizes the risk of unauthorized access and lateral movement within the network. According to research, 72% of organizations are prioritizing zero trust adoption, recognizing its ability to adapt to modern security needs. By focusing on the principle of “never trust, always verify,” ZTNA provides a robust layer of security that helps prevent data breaches.
Cloud Access Security Brokers (CASB)
Think of Cloud Access Security Brokers as the traffic cops of the cloud world. They monitor and control data traffic between users and cloud applications, ensuring that security policies are enforced consistently. CASBs provide visibility into cloud service usage, identify risky behavior, and help prevent data leaks.
With the increasing use of SaaS applications, CASBs have become vital for organizations to maintain control over their data. They offer features like data loss prevention, encryption, and threat protection, making them a crucial component of a comprehensive cloud security strategy.
Data Loss Prevention (DLP)
Data Loss Prevention tools are like a safety net for your data, ensuring it doesn’t slip through the cracks. DLP solutions monitor data in use, in motion, and at rest, detecting potential leaks and preventing unauthorized sharing of sensitive information.
DLP is essential for protecting intellectual property and personal data, especially in industries with stringent compliance requirements. By implementing DLP, organizations can safeguard their data against accidental or malicious loss, ensuring that sensitive information remains secure.
These cloud security solutions—ZTNA, CASB, and DLP—are critical for safeguarding cloud environments in 2024. They help organizations protect their data, prevent unauthorized access, and maintain compliance with regulatory standards. As we continue to steer the complexities of cloud security, these tools offer a robust defense against evolving threats.
Next, we’ll dive into how to choose the right cloud security solution, focusing on public cloud support, compliance standards, and threat detection.
How to Choose the Right Cloud Security Solution
Choosing the right cloud security solution can feel like navigating a maze. But don’t worry, we’re here to guide you through it. Let’s focus on three key areas: public cloud support, compliance standards, and threat detection.
Public Cloud Support
When picking a cloud security solution, check if it supports multiple public cloud providers. This is crucial if your business uses services from giants like AWS, Microsoft Azure, or Google Cloud. Imagine having a tool that lets you manage multiple accounts seamlessly across these platforms. That’s the kind of flexibility you want.
Also, look for solutions that offer granular access control. This means you can decide who gets to use what feature. It’s like having the keys to different rooms in a house, ensuring that only authorized people can enter.
Compliance Standards
Compliance is like the rulebook for cloud security. Your solution should support key compliance standards such as CIS security benchmarks, NIST guidelines, and PCI DSS. These standards ensure that your cloud environment meets the necessary security requirements.
A good solution will also allow you to create custom security policies. This way, you can tailor your security measures to fit your organization’s unique needs. Think of it as customizing a suit to fit perfectly.
Threat Detection
Real-time threat detection is a must-have feature. The solution should alert you to security vulnerabilities as they happen. It’s like having a security alarm that goes off the moment there’s an intrusion.
Check how the solution visualizes these threats and what actionable information it provides. You want a tool that not only tells you there’s a problem but also guides you on how to fix it quickly.
Automated remediation is another key feature. It means the solution can automatically respond to threats, minimizing the time and effort needed from your team. This is like having a self-healing system that addresses issues before they escalate.
By focusing on public cloud support, compliance standards, and threat detection, you can choose a cloud security solution that fits your needs like a glove. Up next, we’ll tackle some frequently asked questions about cloud security solutions, diving into main threats, compliance improvements, and the benefits of cloud-based security.
Frequently Asked Questions about Cloud Security Solutions
What are the main cloud security threats?
Cloud environments face several significant threats. Cyberattacks are at the forefront, with hackers constantly evolving their tactics to breach defenses. These attacks can lead to data theft or even complete shutdowns.
Configuration errors are another common issue. Misconfigured security settings can leave your cloud assets exposed, much like leaving a door open uped. It’s crucial to ensure all settings are correctly configured to avoid potential breaches.
Data leaks can occur accidentally or maliciously, exposing sensitive information. This can damage your reputation and lead to legal issues. Implementing strong security measures can help prevent such leaks.
How do cloud security solutions improve compliance?
Cloud security solutions play a vital role in meeting regulatory frameworks like GDPR and PCI DSS. These frameworks set the standards for how data should be protected. A good security solution will help you align with these standards, ensuring your data practices are up to par.
Data sovereignty is another critical aspect. It refers to the laws governing data storage and transfer across borders. Cloud security solutions assist in managing these complexities, ensuring your data complies with local laws wherever it resides.
Additionally, robust audit processes are essential. These solutions provide detailed logs and reports, making it easier to demonstrate compliance during audits. Think of it as having a detailed map that guides you through the regulatory landscape.
What are the benefits of cloud-based security?
Cloud-based security offers numerous advantages. One of the biggest is lower costs. Since these solutions are hosted in the cloud, there’s no need for expensive on-premises hardware. This can significantly reduce your IT expenses.
Scalability is another benefit. As your business grows, your security needs will too. Cloud-based solutions can easily scale up or down, much like adjusting the size of a balloon. This flexibility ensures you’re always adequately protected.
Finally, these solutions provide faster incident response. With real-time monitoring and automated alerts, you can quickly detect and respond to threats. This swift action can prevent minor issues from becoming major problems, much like stopping a small fire before it spreads.
In the next section, we’ll explore how NetSharx Technology Partners can provide custom solutions to meet your specific cloud security needs.
Conclusion
At NetSharx Technology Partners, we understand that every business is unique, and so are its cloud security needs. This is why we focus on delivering custom solutions that are custom to your specific requirements. Our approach ensures that you get the most effective and efficient security measures without unnecessary extras.
Our unbiased approach sets us apart. As a technology broker, we are not tied to any specific provider, allowing us to offer a wide range of options. We work closely with you to determine the best fit for your organization, leveraging our extensive network of over 330 providers. This means you receive a solution that is not only effective but also cost-efficient.
With our comprehensive support, we guide you through the entire process—from selection to implementation and beyond. Our team of experts is committed to making your cloud security change as seamless as possible. We provide the research, engineering, and analytical resources needed to steer the complex landscape of cloud security.
Choosing the right cloud security solutions is crucial for protecting your data and maintaining compliance. At NetSharx, we pride ourselves on helping you make informed decisions that align with your business goals. Trust us to be your partner in securing your cloud environment, so you can focus on what you do best—growing your business with confidence.
For more information on how we can help you, visit our website or contact us directly. Let’s build a safer future together.