AI-based cybersecurity tools: 5 Powerful Must-Haves for 2025
The Rising Need for AI-Based Cybersecurity Tools
AI-based cybersecurity tools are revolutionizing how organizations detect and respond to cyber threats. Here’s a quick overview of the top AI security solutions currently available:
| Tool Type | What It Does | Key Benefit |
|---|---|---|
| AI Threat Detection | Identifies unknown threats using behavioral analysis | 95.83% faster threat identification |
| User Behavior Analytics | Monitors user actions to spot insider threats | Reduces false positives by up to 86% |
| AI Email Security | Prevents phishing using natural language processing | Stops attacks 99% faster |
| Vulnerability Management | Prioritizes risks using predictive analysis | 38x lighter analyst workload |
| MLSecOps Tools | Secures AI models from adversarial attacks | Protects against AI-specific threats |
In today’s rapidly evolving threat landscape, traditional cybersecurity approaches simply can’t keep pace. With cybercriminals now leveraging AI to create more sophisticated attacks, organizations are facing a 135% increase in novel social engineering attacks and increasingly complex threats that bypass conventional defenses.
“When novel attacks are the new normal, traditional static defenses are no longer enough,” notes a recent industry report from Darktrace. This new reality requires a fundamental shift in how we approach security.
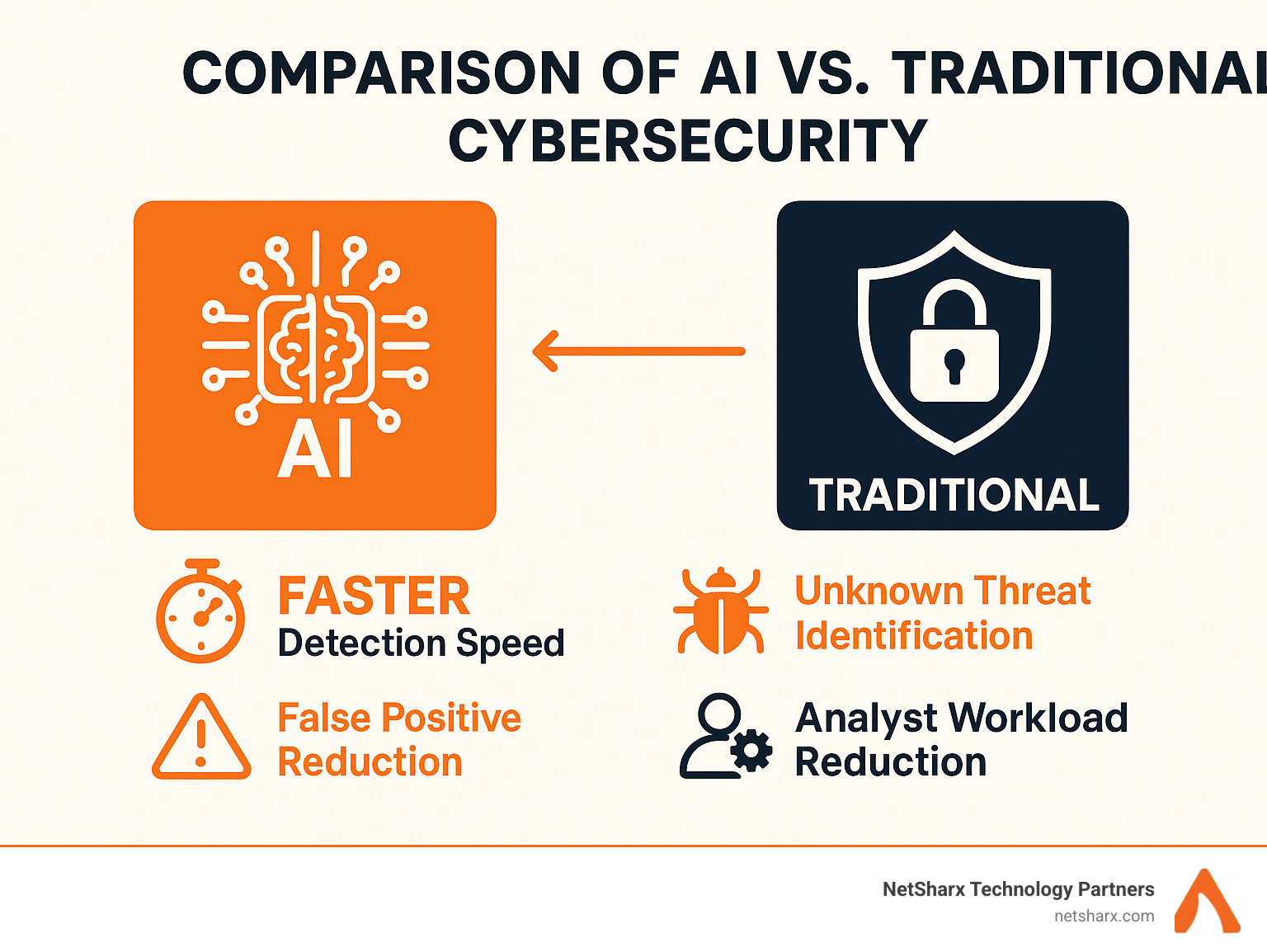
The average time to detect an email attack using legacy solutions is 13 days – an eternity in cybersecurity terms. Meanwhile, organizations using AI-powered tools have reduced their threat identification time by up to 95.83% and can respond to threats in as little as 2.5 minutes.
What makes AI-based security tools so effective is their ability to learn from your organization’s unique data patterns rather than relying solely on known threat signatures. This means they can detect anomalies and potential threats that traditional tools would miss entirely.
As Ryan Carter, founder and CEO of NetSharx Technology Partners, I’ve helped dozens of organizations implement AI-based cybersecurity tools that reduce mean time to respond by 40% without building expensive SOCs or hiring additional security staff.
Why Modern Defenses Need AI
The cybersecurity world has changed dramatically in recent years. In just the first two months of 2023, we saw a shocking 135% jump in clever social engineering attacks. This wasn’t random – it happened right as tools like ChatGPT became popular. What we’re seeing is cybercriminals embracing AI to create more believable, personalized attacks that can target thousands of people at once.
Traditional security tools are like guards who only know how to spot criminals they’ve seen before. They work well enough for familiar threats, but they’re practically blind when faced with these new AI-generated attacks. This security gap isn’t just concerning – it’s creating an urgent need for smarter defense systems.
One financial institution’s security team put it perfectly after adding AI-based cybersecurity tools: “Through one simple integration, completed in just a single day, we were able to add over 50 new threat detections.” This kind of dramatic improvement shows why AI isn’t just helpful – it’s becoming essential.
The numbers behind AI security are genuinely impressive:
- Real estate companies using Darktrace cut their threat identification time by 95.83%
- Manufacturing businesses achieved average response times of just 2.5 minutes
- Healthcare organizations reduced their triage time by a whopping 90%
But the real magic of AI-based cybersecurity tools goes beyond these statistics. They bring capabilities that traditional approaches simply can’t match.
First, they’re constantly learning from your specific environment. Unlike one-size-fits-all solutions, AI builds security models custom specifically to your organization’s unique patterns and behaviors.
Second, AI can analyze massive amounts of data in real-time, spotting subtle patterns that would be impossible for human analysts to catch. Think of it as having thousands of security experts working simultaneously, 24/7, without coffee breaks.
Third, instead of just reacting to attacks that have already happened, AI can predict potential threats before they materialize. It’s like having a security system that not only responds to break-ins but anticipates where and how they might occur.
Finally, advanced AI systems can take immediate action when they spot something suspicious. This autonomous response capability contains threats before significant damage occurs, often resolving situations before a human would even notice them.
As one CISO beautifully summarized: “AI enables a shift from reactive responses to proactive protection.” This fundamental change explains why over 70% of organizations now use managed AI services in their cloud environments – adoption rates nearly matching those of managed Kubernetes (80%).
The research backs this up too. According to scientific research on AI-driven threat reduction, organizations implementing AI security tools see substantially improved threat detection capabilities while simultaneously reducing analyst workload and alert fatigue.
At NetSharx Technology Partners, we’ve seen how AI-based cybersecurity tools transform security operations from reactive to proactive, giving our clients peace of mind in an increasingly complex threat landscape.
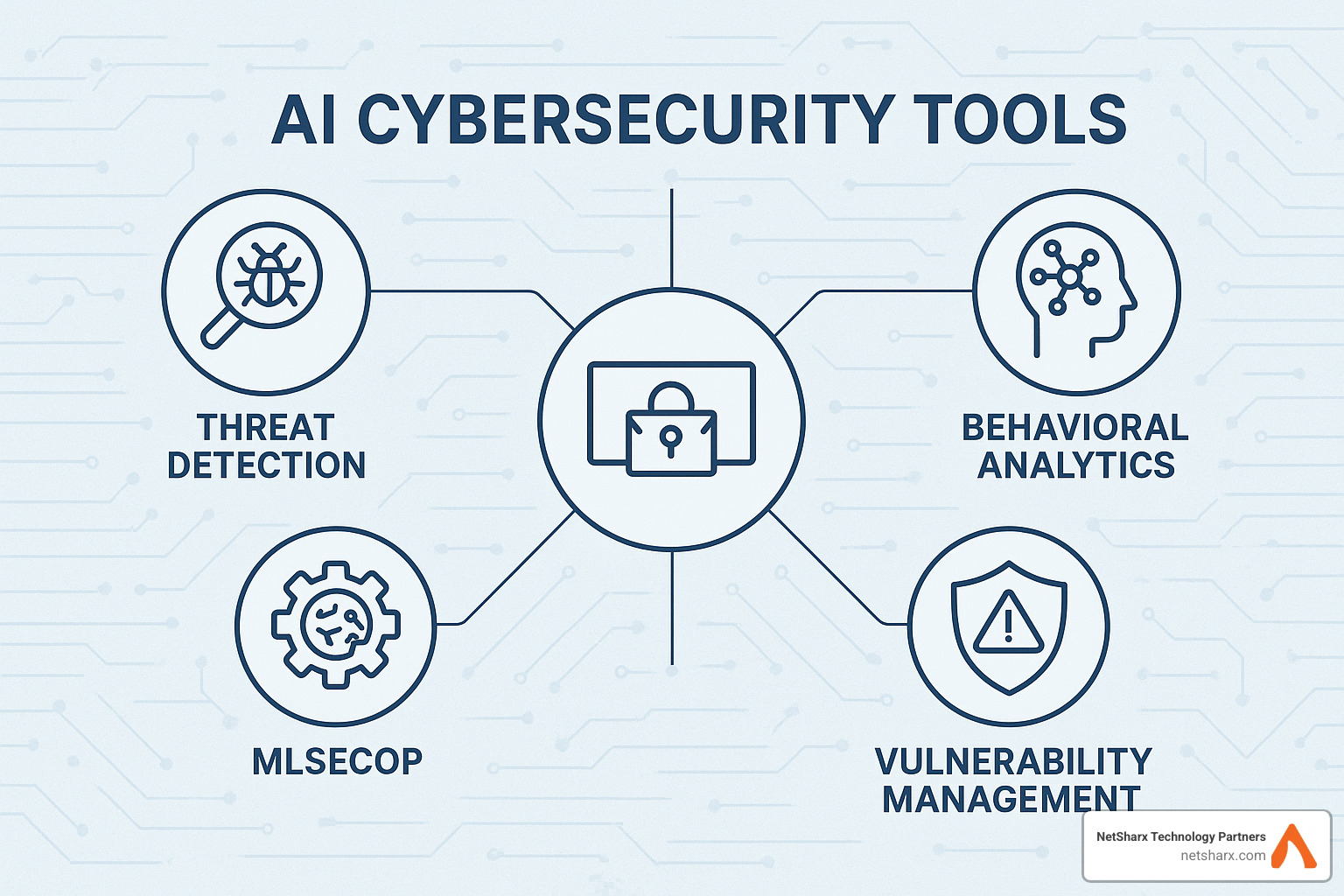
5 Must-Have AI-Based Cybersecurity Tools for 2025
Looking ahead to 2025, several game-changing AI-based cybersecurity tools are becoming essential for organizations serious about their security. These aren’t just incremental improvements on old tech – they represent a fundamental shift in how we protect our digital assets, using advanced machine learning that actually learns and adapts alongside evolving threats.
AI Threat Detection & Response Platforms
Think of these platforms as the brain of your security operation – constantly monitoring, learning, and protecting your entire digital environment. What makes them special is how they build custom behavioral models specific to your organization, understanding what “normal” looks like so they can spot the abnormal.
I recently worked with a manufacturing client who implemented Vectra AI’s platform. Within the first month, they were amazed at how it eliminated 80% of the noise that used to overwhelm their security team. “It’s like finally being able to hear someone whispering in a crowded room,” their CISO told me.
The impact on response time is nothing short of dramatic. Without AI, the average breach can take 10 months to contain. With these tools? Often just 10 minutes. That’s the difference between a catastrophic breach and a minor incident.
The best platforms include anomaly detection engines that spot unusual behavior, autonomous response capabilities to contain threats automatically, SOAR integration for coordinated responses, and unified visibility across your entire environment. When a ransomware attempt hit one of our clients, their AI system detected and contained it within minutes – saving what could have been millions in damages.
Behavioral Analytics & UEBA (User & Entity Behavior Analytics)
While traditional security focuses on known threats, UEBA tools take a different approach by understanding how your users and systems typically behave. When something doesn’t fit the pattern – even if it’s technically “allowed” – these tools raise a flag.
This approach is particularly effective against insider threats and account takeovers, which increased by a shocking 52% in mid-2023. As one IT director told me after implementing these tools, “It’s like having a security guard who knows everyone in the building by name and can immediately spot when someone’s acting strangely.”
Modern UEBA platforms create detailed behavioral baselines for each user and entity, identify potential insider threats through pattern analysis, use deviation scoring to prioritize the most suspicious activities, and can even adjust authentication requirements based on risk factors.
One healthcare organization finded an unauthorized user accessing patient records at 2 AM – something their traditional tools completely missed because the user had valid credentials. The AI flagged the unusual timing and access pattern, allowing the team to immediately lock down the account and prevent a data breach.
AI-Driven Email & Phishing Defense
Email remains the number one way attackers get into organizations, and with AI-generated phishing attempts becoming increasingly sophisticated, traditional filters just can’t keep up. Modern email security now uses advanced AI to analyze everything from writing style to sender behavior.
These tools can spot the subtle signs that a human would miss – like tiny variations in domain names or slight changes in how an executive phrases requests. “It’s uncanny how good these systems have become,” a client recently told me. “Last month, our AI caught an email that looked exactly like something our CFO would send – except it wasn’t him.”
The best email security platforms use natural language analysis to detect social engineering, identify brand impersonation attempts, prevent account takeovers by spotting unusual sending patterns, and even provide coaching to help users recognize threats themselves.
One financial services firm I work with reduced their phishing susceptibility by 87% in just six months after implementing AI-based email security. That’s the kind of improvement that fundamentally changes your security posture.
AI for Vulnerability Management & Attack-Surface Monitoring
The sheer number of vulnerabilities finded each year is overwhelming – no team has enough resources to patch everything. AI-powered vulnerability management helps you focus on what actually matters in your specific environment.
These tools look beyond basic severity scores to consider factors like asset importance, network exposure, threat intelligence, and exploit availability. As one security engineer put it, “It’s like having a security expert who knows your entire environment inside and out, helping you decide what to fix first.”
The best platforms offer predictive risk scoring custom to your environment, automated code scanning for custom applications, attack path visualization to understand complex vulnerability chains, and continuous monitoring to identify new exposure points as they appear.
A government agency client of ours cut their vulnerability remediation time from weeks to days by focusing only on the issues their AI platform identified as truly critical. They achieved better security outcomes while dramatically reducing their workload – the best of both worlds.
MLSecOps & AI Infrastructure Protection
As more organizations deploy their own AI systems, securing those systems has become a critical concern. MLSecOps tools protect your AI investments from manipulation, data poisoning, and model theft.
“Most organizations are just beginning to realize they need to secure their AI systems,” a security architect recently told me. “It’s like we’ve built sophisticated new weapons but forgotten to lock the armory.”
This emerging field focuses on model hardening to resist adversarial attacks, adversarial testing frameworks like the Adversarial Robustness Toolbox, privacy auditing tools to detect data leakage, and AI vulnerability scanners for testing large language models.
At NetSharx Technology Partners, we’ve helped numerous clients implement MLSecOps programs that protect their AI investments while maintaining compliance with emerging regulations like the EU AI Act. As one client put it, “We didn’t even know what we didn’t know about AI security until NetSharx helped us build a protection strategy.”
With the right AI-based cybersecurity tools in place, you’re not just defending against today’s threats – you’re building an adaptive immune system that evolves alongside the threat landscape. That’s the kind of future-proofing every organization needs heading into 2025.
How AI-Based Cybersecurity Tools Detect Unknown Threats
The most remarkable capability of AI-based cybersecurity tools is their ability to identify threats that have never been seen before – something traditional security tools simply cannot do. This capability is critical in an era where attackers continuously develop novel techniques to evade detection.
At the heart of this capability are several advanced AI technologies that work together to create a security system that learns, adapts, and improves over time.
Machine Learning Pipelines
Think of machine learning pipelines as assembly lines for threat detection. They take in massive amounts of raw security data and transform it into actionable intelligence through a series of sophisticated steps.
First, these systems gather and standardize security data from across your organization – everything from email logs to network traffic. Next, they extract the meaningful patterns and characteristics that might signal something fishy. The AI then builds detection models based on both known threats and what normal behavior looks like in your specific environment.
What’s truly impressive is how these systems apply their models in real-time. As one customer told us, “It’s like having a security analyst who never sleeps and can watch everything at once.”
“Qevlar AI operates fully autonomously without human prompts or pre-existing playbooks, pulling and enriching data from all tools to determine maliciousness before any human oversight,” explains one AI security vendor. This independence allows these tools to spot threats at speeds no human team could match.
Unsupervised Learning and Clustering
One of the most powerful approaches in AI security is unsupervised learning – the ability to spot unusual patterns without needing examples of what threats look like. This is particularly valuable for catching zero-day attacks that have never been seen before.
CISA, the U.S. Cybersecurity and Infrastructure Security Agency, uses “unsupervised machine learning for real-time network anomaly detection” in its CyberSentry program. This approach lets them sift through terabytes of network data daily to find the needles in the haystack.
I recently worked with a manufacturing client who finded a sophisticated data theft attempt that had been going on for months. Their AI-based cybersecurity tools flagged unusual data transfers happening in the middle of the night – a subtle pattern that their traditional security tools had completely missed. The AI didn’t know exactly what the attack was, but it recognized that something wasn’t right.
Reinforcement Learning Loops
The best AI security systems get smarter over time through reinforcement learning. Each time they correctly identify a threat – or make a mistake – they learn from the experience and improve their detection capabilities.
“Continuous learning from analyst feedback enables the AI to adapt dynamically to an organization’s changing environment,” notes a leading security vendor. This creates a virtuous cycle where your security system becomes more attuned to your specific business and the threats you face.
When your team confirms or corrects an AI detection, you’re not just handling that specific incident – you’re making your entire security system more effective for the future. It’s like having a security team that gets better with every day on the job.
Threat Intelligence Fusion
One of AI’s superpowers is connecting dots across different data sources. By combining threat intelligence feeds, internal telemetry, and global attack patterns, AI can spot relationships that would be impossible for human analysts to find.
“MixMode’s Third Wave AI built on a dynamical threat detection foundation model” claims to forecast expected network behavior in less than seven days without human input. This self-supervised learning approach helps the system understand what’s normal for your specific environment and immediately flag anything unusual.
The real-world impact is dramatic. Organizations using advanced AI detection typically identify and respond to threats in minutes rather than the days or weeks required with traditional approaches. As one customer reported, “Fletch has saved me time because I’m looking at stuff that actually matters” – a testament to AI’s ability to cut through the noise and focus security teams on genuine threats.
At NetSharx Technology Partners, we’ve seen how these AI-based cybersecurity tools transform security operations from reactive to proactive, giving our clients peace of mind in an increasingly complex threat landscape.
Implementation Challenges & Best Practices
Let’s be honest – implementing AI-based cybersecurity tools isn’t always smooth sailing. Even with their amazing capabilities, there are real challenges you’ll face along the way. At NetSharx, we’ve guided dozens of clients through this journey, and we’ve learned what works (and what definitely doesn’t).
Managing False Positives
The first thing most of our clients notice? The alerts. So. Many. Alerts.
When you first deploy AI security tools, finding the right sensitivity balance feels a bit like adjusting the temperature in your office – too hot and everyone complains, too cold and, well, everyone still complains.
“The first week was overwhelming,” one of our financial clients told me. “We were drowning in alerts. But after a proper tuning period, the system eliminated about 80% of those false positives.”
The secret? Start with a learning phase where you monitor alerts without taking automatic action. This gives your team time to provide feedback, marking what’s truly suspicious versus normal business activity. Think of it as training a new security analyst – they need time to understand what’s normal in your environment.
As confidence builds, you can gradually increase automation. One manufacturing client started with just email security automation, then expanded to endpoint response once they trusted the system’s judgment.
Integration Complexity
Let’s not sugarcoat it – getting AI tools to play nice with your existing security stack can be challenging. Most organizations have accumulated a patchwork of security solutions over the years, and now you’re asking them all to share data with a new AI system.
One healthcare client described their integration experience as “trying to get all my specialists to talk to each other about my health.” An apt comparison!
To avoid integration headaches, conduct a thorough inventory of your current systems first. Know what you have before adding something new. When selecting AI tools, prioritize those with pre-built connectors for your critical systems – this can save weeks of custom integration work.
Consider a phased implementation approach rather than attempting to boil the ocean. One retail client started by integrating their email security and endpoint protection first, then gradually added network monitoring and cloud security in subsequent phases.
Data Governance and Privacy
AI needs data to learn – and lots of it. But this raises obvious questions: What data are you feeding it? Where is that data stored? Who has access to it?
“We were excited about the AI capabilities until our legal team asked about GDPR compliance,” a European client told us. “That stopped us in our tracks for weeks.”
Smart organizations define clear data boundaries from the start. Be explicit about what data can be used for AI training and what must remain off-limits. Many of our clients opt to keep all models and data in-house rather than using cloud-based AI that might send sensitive information outside their environment.
Remember to regularly audit your data usage. AI systems have a tendency to expand their data collection over time, so what started as compliant might drift if not monitored.
Skills and Training Requirements
The skills gap is real. Your existing security team might be excellent at traditional security operations but completely unfamiliar with machine learning concepts or how to interpret AI-generated insights.
“My team was skeptical at first,” admitted the CISO of a manufacturing client. “They saw the AI as a threat to their jobs rather than a tool to make them more effective.”
Successful implementations include dedicated training time for security analysts. This isn’t just about how to use the tool’s interface – it’s about understanding AI concepts, knowing when to trust the system’s recommendations, and when human judgment should override automated suggestions.
For smaller teams, managed or co-managed services can bridge the skills gap. Several of our clients started with our managed AI security service before gradually bringing capabilities in-house as their team developed expertise.
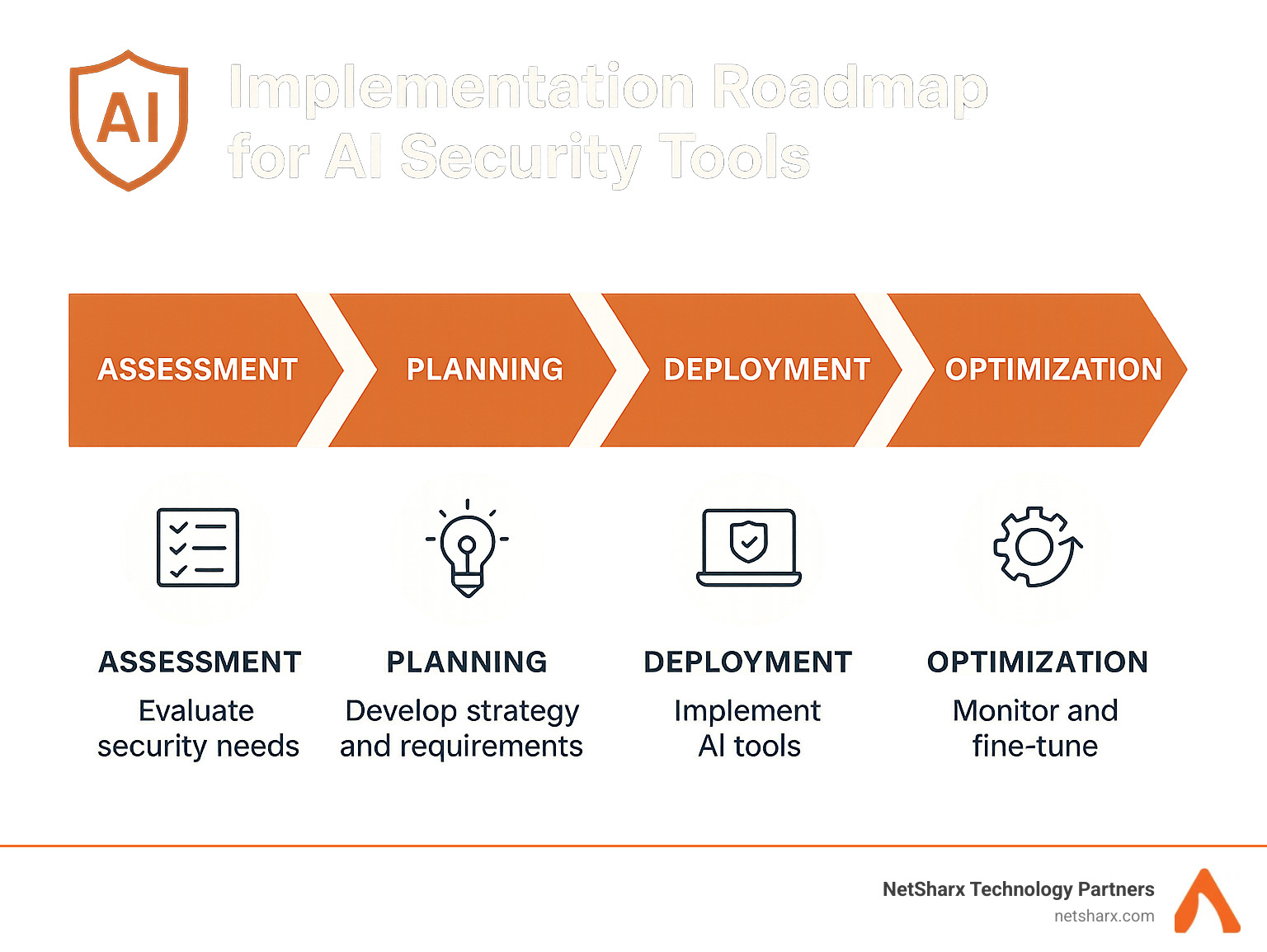
Phased Implementation Approach
Rome wasn’t built in a day, and neither is an effective AI security program. The organizations that see the most success take a measured, phased approach.
A typical roadmap we recommend includes four distinct phases:
First, an assessment phase where you evaluate your current security posture and identify your highest-priority use cases. For one financial client, this was detecting account takeover attempts; for a healthcare organization, it was protecting patient data from insider threats.
Next comes the pilot phase, where you deploy AI tools in a limited scope. This controlled environment lets you validate effectiveness without disrupting your entire security operation.
The expansion phase follows, gradually extending coverage to additional systems and use cases. Finally, you enter the optimization phase, continuously refining models and automation based on real-world results.
“We saw immediate improvements in threat detection during our pilot,” shared one client, “but the real change came during the optimization phase when the system had learned enough about our environment to make truly intelligent decisions.”
Zero-Trust Alignment
AI-based cybersecurity tools work best when they’re part of a coherent security strategy, not bolted on as an afterthought. We’ve found the most successful implementations align with zero-trust principles.
This means using AI insights to enforce continuous verification of all users and systems, rather than trusting anything implicitly. It means implementing least-privilege access controls and using AI to detect when someone is attempting to access resources beyond what they need.
“Our AI tools became exponentially more effective when we segmented our network properly,” explained one client. The segmentation limited potential lateral movement, while the AI excelled at spotting attempts to cross those boundaries.
At NetSharx Technology Partners, we believe in making complex technology simple. AI security doesn’t have to be overwhelming. With the right planning, realistic expectations, and a methodical approach, you can harness these powerful tools to dramatically improve your security posture – without the implementation headaches that too many organizations experience.
Frequently Asked Questions About AI-Based Cybersecurity Tools
What differentiates AI-based cybersecurity tools from legacy solutions?
When clients ask me what makes AI-based cybersecurity tools so different from traditional security solutions, I like to explain it through a simple analogy: traditional tools are like security guards with a checklist, while AI tools are like experienced detectives who notice when something just feels “off.”
Traditional security relies heavily on predefined rules – essentially saying “if you see X, then it’s a threat.” These systems can only catch what they’ve been specifically programmed to find. They’re reactive by nature, waiting for known threats to appear.
AI-based cybersecurity tools, on the other hand, learn what’s normal in your environment and then flag anything unusual. As one of our clients put it after implementing an AI security platform: “We finally found an AI model handling 90% of routine alerts, allowing our team to focus on strategic security initiatives rather than alert triage.”
The speed difference is dramatic too. While traditional tools might take hours or days to identify threats, Darktrace customers report achieving “a 2.5 minute average time to respond to threats.” This rapid response can mean the difference between a minor security incident and a major breach.
Perhaps most importantly, AI systems can identify threats nobody has seen before. In today’s landscape where attackers are constantly developing new techniques, this ability to spot the unknown is invaluable. As one security expert explained, “AI enables a shift from reactive responses to proactive protection.”
How do these tools stay ahead of AI-powered attackers?
It’s a bit like an arms race – as attackers adopt AI to create more sophisticated threats, defenders must leverage even more advanced AI to stay ahead. This is where modern AI-based cybersecurity tools really shine.
Today’s security platforms use several sophisticated approaches to maintain their edge. They incorporate adversarial machine learning techniques that essentially allow them to think like attackers, anticipating how malicious actors might try to evade detection.
The learning never stops, either. As one vendor explained, “AI algorithms improve over time as they learn from specific business environments.” This continuous adaptation means the defensive AI gets smarter with every attack it encounters.
Global threat intelligence plays a crucial role too. By connecting to worldwide security networks, your AI tools can learn from attacks targeting other organizations before they ever reach your systems. It’s like having an early warning system that spans the entire internet.
I was particularly impressed when one of our clients shared how their AI security system detected an attack pattern that had just emerged in Asia before it hit their North American operations. This proactive protection is simply impossible with traditional tools.
One security researcher summed it up nicely: “Generative AI can simulate and model potential attack scenarios to preempt threats.” By constantly running simulations of possible attacks, modern security AI stays several steps ahead of the bad guys.
What should organizations evaluate when selecting an AI security platform?
Choosing the right AI-based cybersecurity tools for your organization is a bit like hiring a new security team – you need to make sure they’ll work well with your existing staff, understand your environment, and communicate clearly when something’s wrong.
Integration capabilities should top your evaluation list. As one of our security consultants often advises clients, “Assess each tool’s integration compatibility with your current technology stack.” The most powerful AI in the world won’t help if it can’t connect to your systems.
Detection accuracy is equally crucial. I’ve seen organizations struggle with AI tools that generate too many false positives, creating alert fatigue. As one CISO told me, “We needed a solution that could reduce alert noise without missing critical threats.” Ask vendors for specific metrics about their false positive rates in environments similar to yours.
Look for transparency and explainability in how the AI makes decisions. Security teams need to understand why alerts are generated to take appropriate action. One vendor proudly describes their approach as “not a black box,” which is exactly what you want – an AI that can explain its reasoning.
Consider the operational overhead required to deploy and maintain the solution. One frustrated security director shared with me that “tools that aren’t intuitive waste precious hours training employees.” The best AI security tools are powerful yet straightforward to use.
Finally, ensure the solution can scale with your organization. As our implementation specialists at NetSharx Technology Partners often recommend, “Prioritize scalability and ease of use to minimize training overhead.”
When helping clients evaluate options, we always start by understanding their specific security objectives and existing gaps before recommending particular tools. And we typically suggest solutions that “integrate seamlessly with major platforms like Microsoft 365 or Google Workspace” to minimize disruption while maximizing security benefits.
The right AI-based cybersecurity tools should feel like an extension of your security team – working tirelessly in the background, highlighting what truly matters, and helping you stay ahead of threats in an increasingly complex digital landscape.
Conclusion
The cybersecurity landscape has fundamentally changed. With attackers now leveraging AI to create increasingly sophisticated threats, organizations must adopt AI-based cybersecurity tools to maintain effective defenses. As we’ve explored throughout this article, these advanced solutions offer capabilities that traditional security approaches simply cannot match.
The numbers don’t lie – and they’re pretty impressive. We’re talking about 95.83% faster threat identification, 86% fewer false positives, and response times measured in minutes instead of days or weeks. This isn’t just a small step forward – it’s a giant leap in how we approach cybersecurity.
One security expert put it perfectly: “AI is truly changing cybersecurity with human-like intelligence at machine scale.” This change allows organizations to not just keep up with evolving threats but to get ahead of them, identifying and stopping risks before they become major problems.
If you’re thinking about implementing AI security tools, here are a few friendly pieces of advice:
First, start with clear objectives. Figure out where your biggest security gaps are and focus your AI implementations there. There’s no need to overhaul everything at once.
Second, take a phased approach. Begin with those high-value areas we just mentioned and expand as your team gets more comfortable with these new AI-driven tools.
Third, invest in your people. Even the best tools need skilled hands to guide them, so make sure your security team has the training they need to make the most of AI capabilities.
Finally, keep humans in the loop. AI is amazing at efficiency and scale, but your team’s expertise remains essential for making strategic security decisions. The best approach combines AI’s processing power with human judgment.
At NetSharx Technology Partners, we help organizations steer the sometimes confusing world of AI-based cybersecurity tools. We pride ourselves on our vendor-agnostic approach – we recommend solutions based on what you actually need, not on which vendors are offering the best commissions.
As threats continue to evolve, one thing is becoming increasingly clear: organizations that successfully implement AI security tools will have a significant advantage in protecting their digital assets. The question isn’t whether to adopt AI for cybersecurity anymore – it’s how to implement it most effectively for your specific needs.
Ready to see how AI-based security tools can strengthen your defenses? Reach out to NetSharx Technology Partners today for a friendly conversation about your organization’s unique security challenges. We’re here to help you build a more secure future.